On Fri, 08 Nov. 2024 my team- Fr334aks-mini participated in Bluehens CTF 2024 - a jeopardy-style Capture The Flag (CTF) competition organized by the University of Delaware’s own CTF team in collaboration with BSides Delaware.
Fr334aks-mini secured position 223 out of 498 teams globally, reflecting our growing experience and commitment to learning in this competitive arena. The challenges were diverse and well-crafted, covering a range of categories that pushed us to think critically.
In this write-up, I will share some insights from the competition. Each challenge, regardless of its difficulty, contributed to our growth and has motivated us to aim even higher in future competitions.
OSINT
Training Problem: Intro to OSINT
We are given an image “osint1.png” and a description
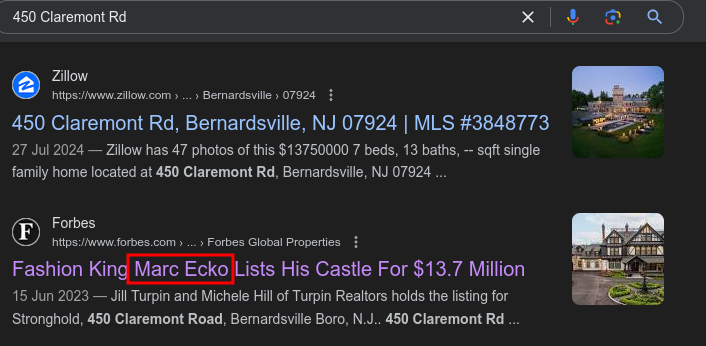
A famous person is selling their house. In this market, who wouldn’t? Can you tell me who owns this house, and what the license plate of their “tough” car is?
Flag format: udctf{FirstLast_licenseplate}
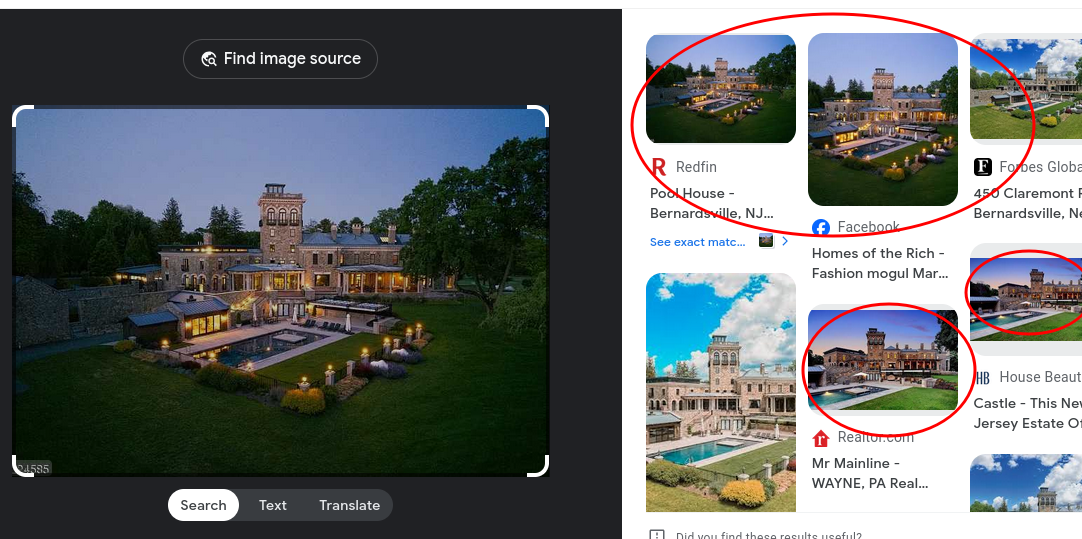
Doing reverse image search in google we find several instances of the image
Seems someone is truly tired of his house. Let’s find out who?
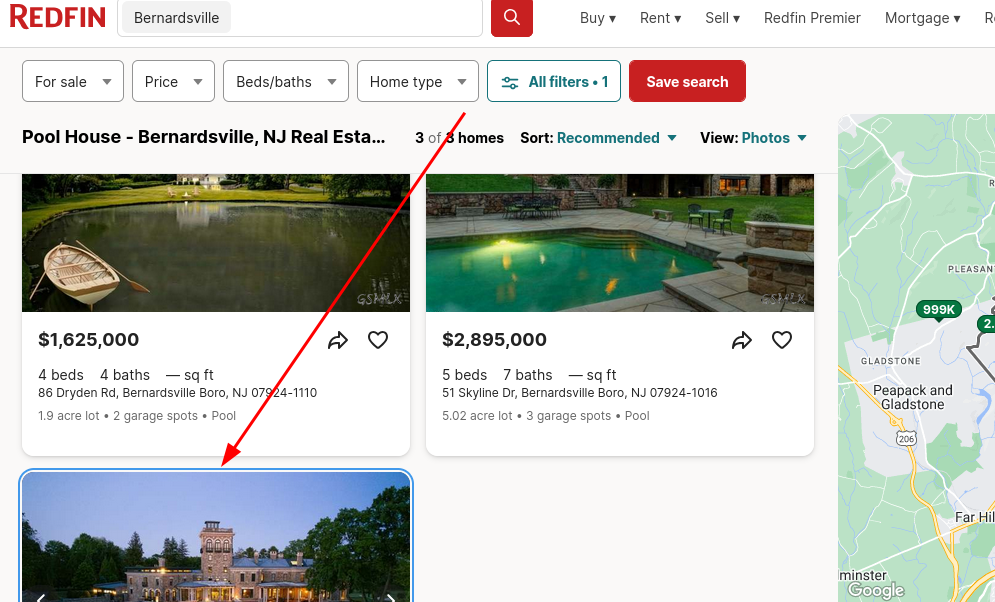
Checking out the image link, we have some specifics.
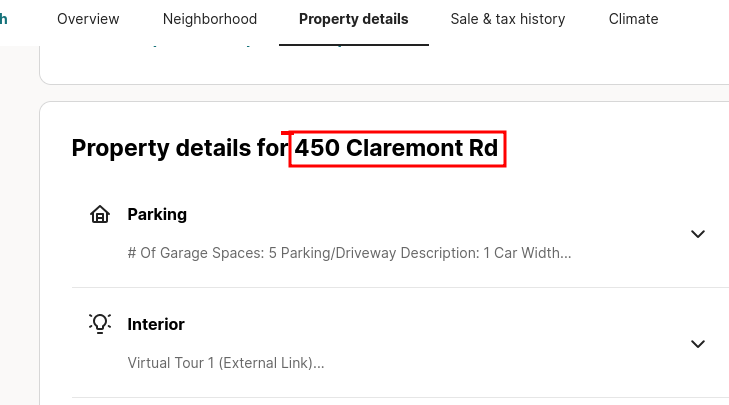
Let’s take a look at that address, and sure we have a name!
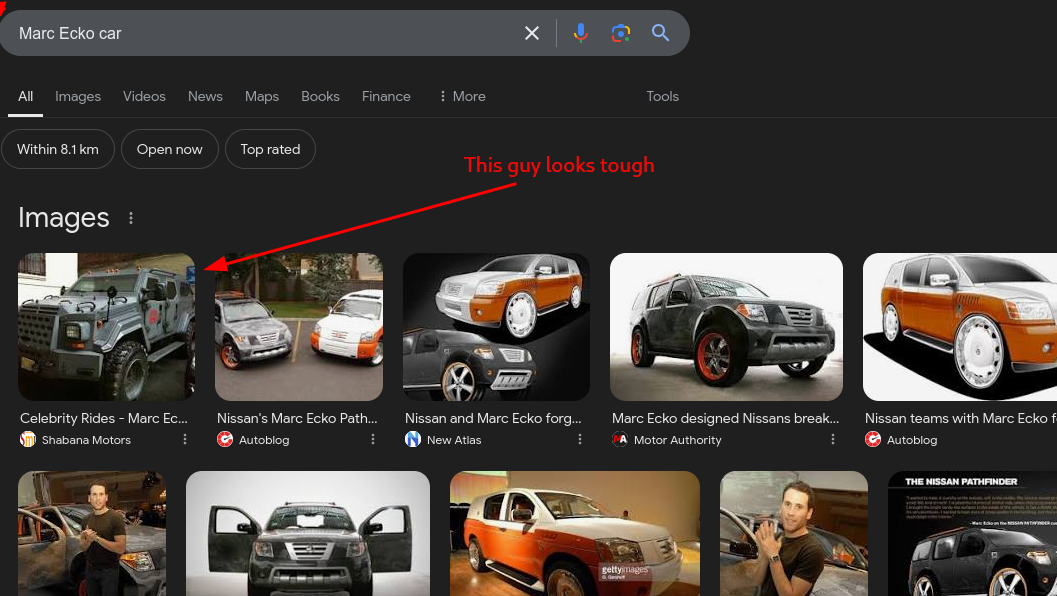
Looking around for his car, He really likes cars
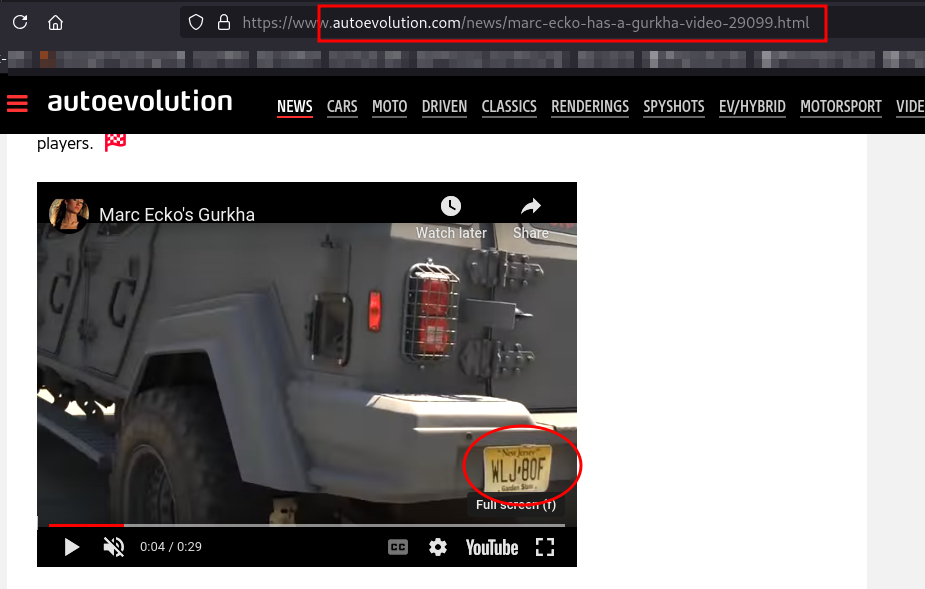
I landed into this page with a short video
We now have a fully built tough flag
udctf{MarcEcko_WLJ-80F}
Forensics
a. Inner Demons
We are given an image with the description - I can’t seem to sleep at night… Maybe I need to dig further within.
Suspecting steganography, I used StegSeek, a powerful tool for uncovering hidden content in JPEG files, to analyze the image.
Steps to Solve:
Running StegSeek:
I executed the following command:
1 2
stegseek inner_demons.jpgStegSeek scanned the file for steganographic content embedded with a passphrase.
Tool Output:
The tool successfully identified a hidden file using the passphrase
junji. The hidden data was in a file namedflag.txtoriginally. It extracted the concealed content and saved it toinner_demons.jpg.outReading the Extracted Content:
I inspected the output file with:
1 2
cat inner_demons.jpg.outThis revealed the flag:
udctf{h0w_d0_y0u_s133p_@t_n1ght?}
b. Whispers of the Feathered Messenger
This challenge required unraveling multiple layers of hidden data to uncover the flag. Here’s the step-by-step breakdown of my solution:
Steps to Solve:
Identifying the File Type:
I began by inspecting the file provided using the
filecommand:1 2
file bird.jpegExtracting Metadata:
To explore hidden information, I ran
exiftoolon the image:1 2
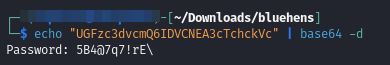
exiftool bird.jpegThe output included a comment field containing this cool string:
1 2
Comment: UGFzc3dvcmQ6IDVCNEA3cTchckVcDecoding the Comment:
Suspecting Base64 encoding, I decoded the string using:
This revealed a password:
1
2
5B4@7q7!rE\
Using Steghide:
With the password in hand, I utilized
steghideto extract hidden data from the image:1 2
steghide extract -sf bird.jpeg -p '5B4@7q7!rE\'
This produced a file named
encrypted_flag.bin.Analyzing the Extracted File:
Running the
filecommand onencrypted_flag.binidentified it as an OpenSSL-encrypted file.Decrypting with OpenSSL:
Referring to this guide, I decrypted the file using:
1 2
openssl enc -d -aes-256-cbc -in encrypted_flag.bin -out decrypted_flag -pass pass:'5B4@7q7!rE\'
Retrieving the Flag:
Viewing the decrypted output revealed the flag:
UDCTF{m0AybE_YoR3$!_a_f0recnicsEs_3xpEr^t}
XOR
XS1: XOR without XOR
The title hinted at solving the problem “without XOR,” suggesting the need to explore alternative methods beyond brute force or direct XOR operations.
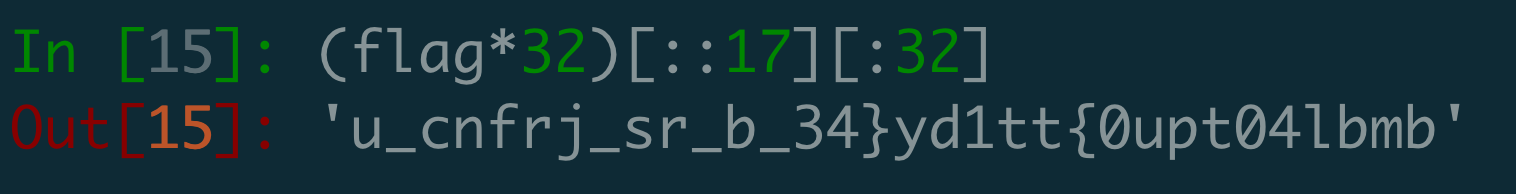
Looking at the nature of the problem image and the hint in the title, I believed that the string had been manipulated in a reversible manner, possibly by reversing and slicing.
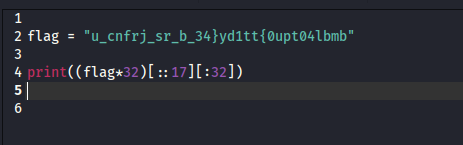
I made a python script to reverse the reversed flag
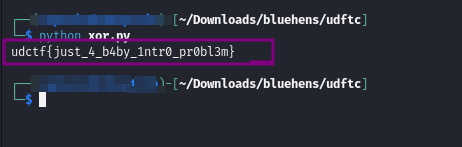
Running her:
udctf{just_4_b4by_1ntr0_pr0bl3m}
Big thanks to my team mates. Till next time, cheers!
And remember, there are many ways of killing a rat!