This weekend I Participated in Patriot CTF 2023 alongside my team Fr334aks-Mini.
It was a jeopardy style ctf organised by the CyberSec club of George Mason University, MasonCC and these are some of the challenges I solved.
1. Forensics
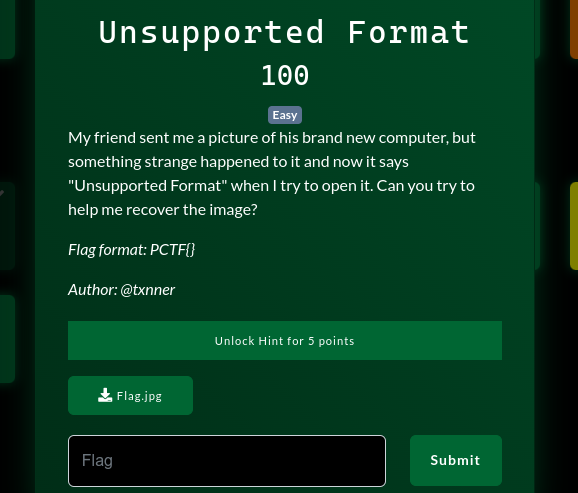
a. Unsupported Format
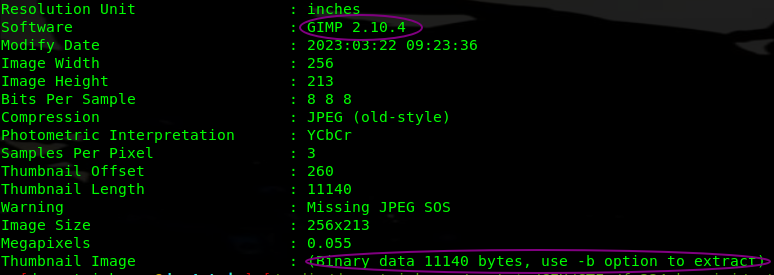
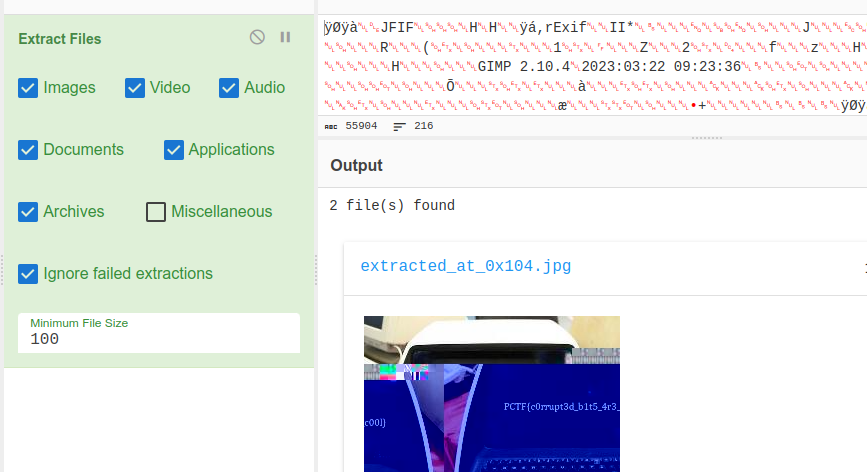
We are given a Flag.jpeg file which could not be opened. Checked it’s metadata with exiftool and noticed something: GIMP and some embeded binary data.
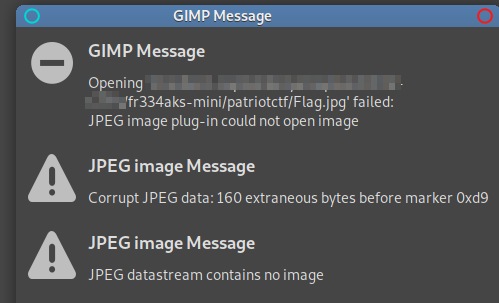
Opening the image with GIMP didn’t really help.
With cyberchef, I extracted a hidden image file.
PCTF{c0rrupt3d_b1t5_4r3_c00l}
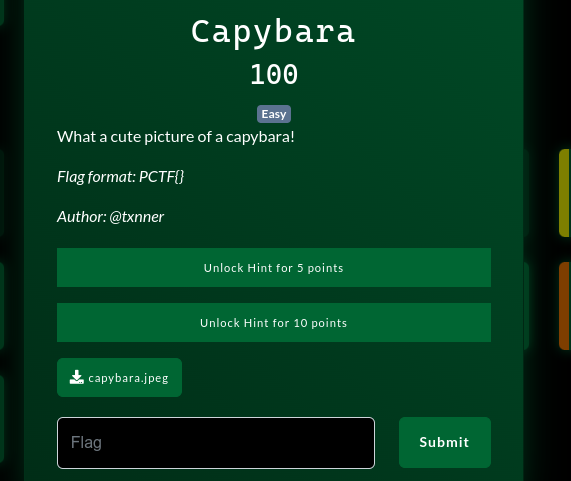
b. Capybara
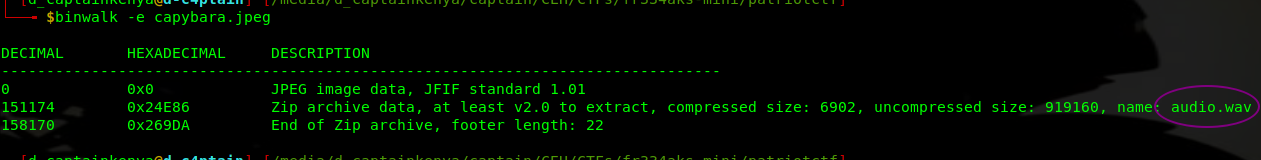
We are given an image of a capybara.
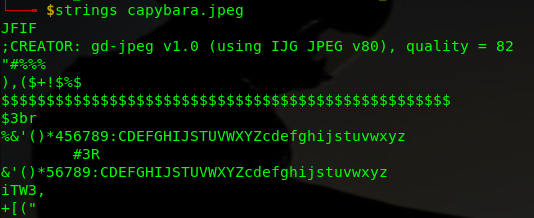
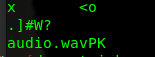
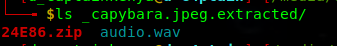
Checking the strings, there was several occurences of audio.wav
We go on to extract the audio file with binwalk.
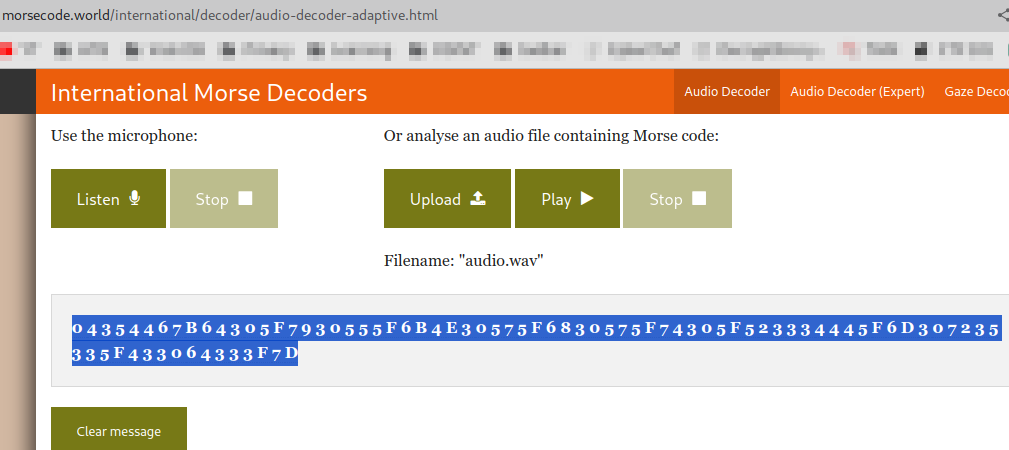
Playing the audio showed it was on morse code. Let’s decode it here
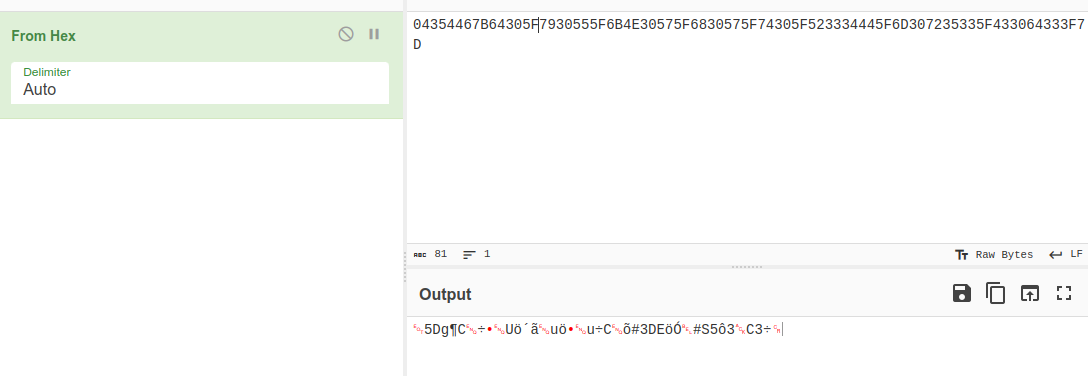
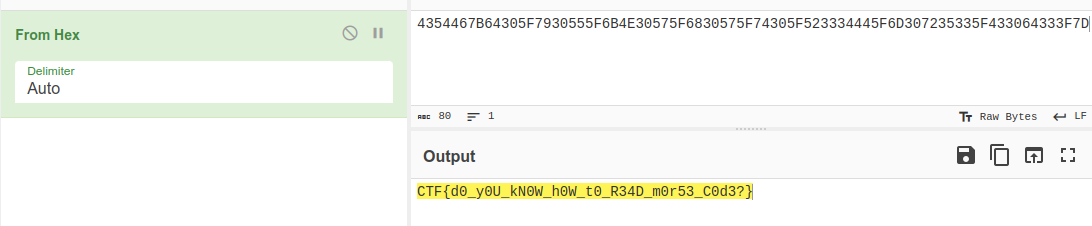
We get some hex data.
Decoding it directly didn’t work so I tickled the leading character-zero.
PCTF{d0_y0U_kN0W_h0W_t0_R34D_m0r53_C0d3?}
2. Crypto
a. Multi-numeral
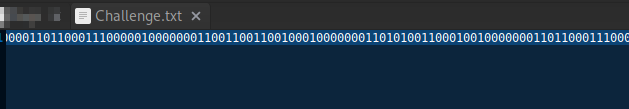
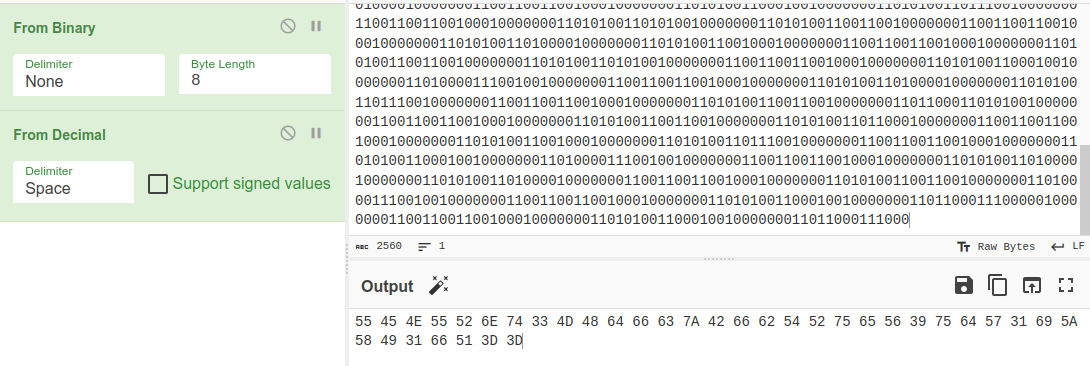
We have a txt file with some binary data.
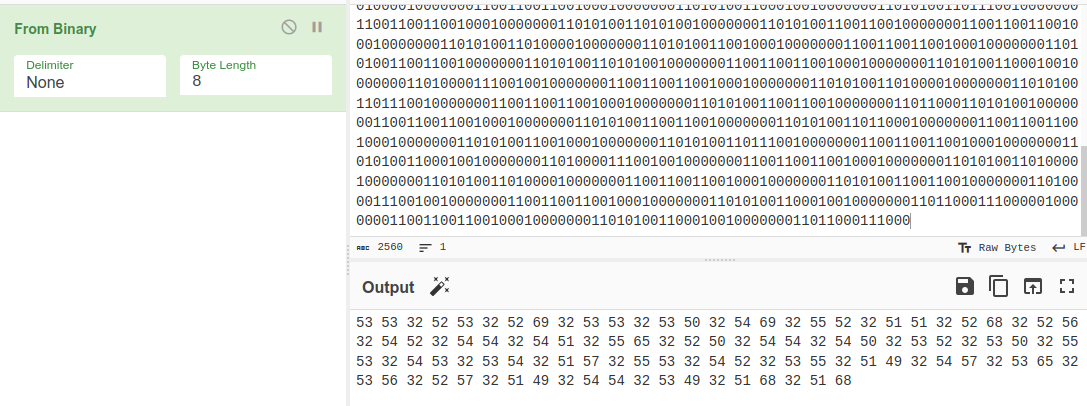
Decoding it gives data in decimal representation.
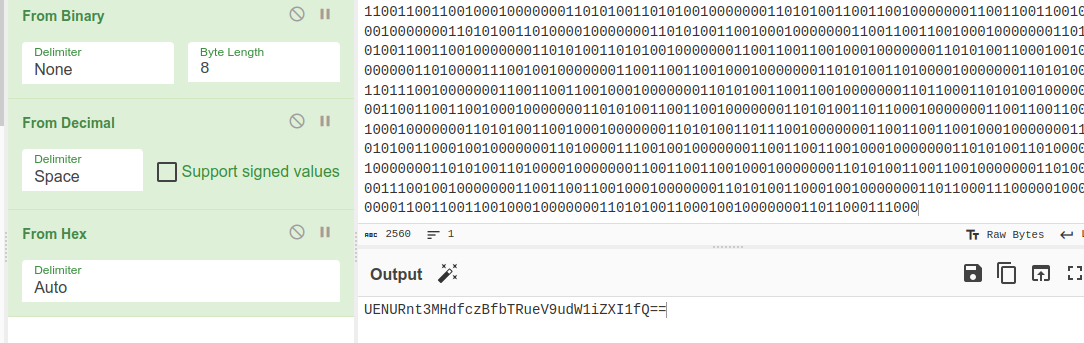
After decoding it we have hex values
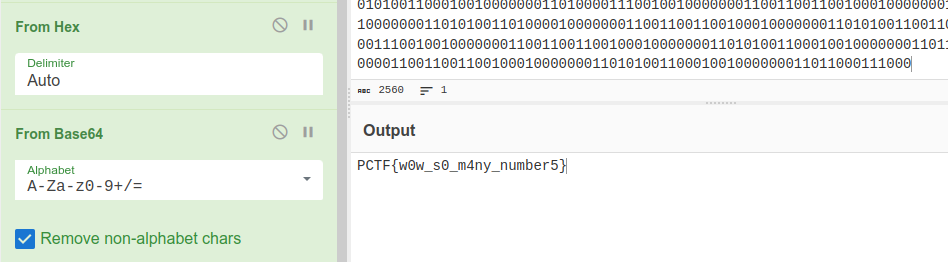
Thi further leads to a base64 string.
After decoding it we have our flag.
PCTF{w0w_s0_m4ny_number5}
3. OSINT
a. Bad Documentation
We are given a github repo in which a security researcher leaked his password.
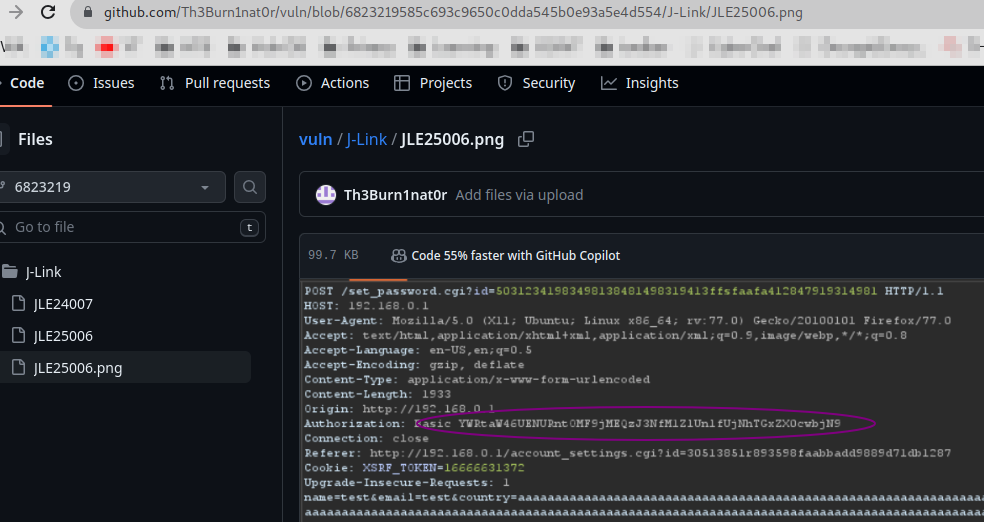
Opening the repo, I found 8 commits. I browsed around the history points of the commits till I found this: https://github.com/Th3Burn1nat0r/vuln/blob/6823219585c693c9650c0dda545b0e93a5e4d554/J-Link/JLE25006.png
I saw an Authorization header using Basic which utilizes base64 encoding. Decoding it, we see the plain password.
PCTF{N0_c0D3's_3VeRy_R3aLlY_G0n3}
4. Misc
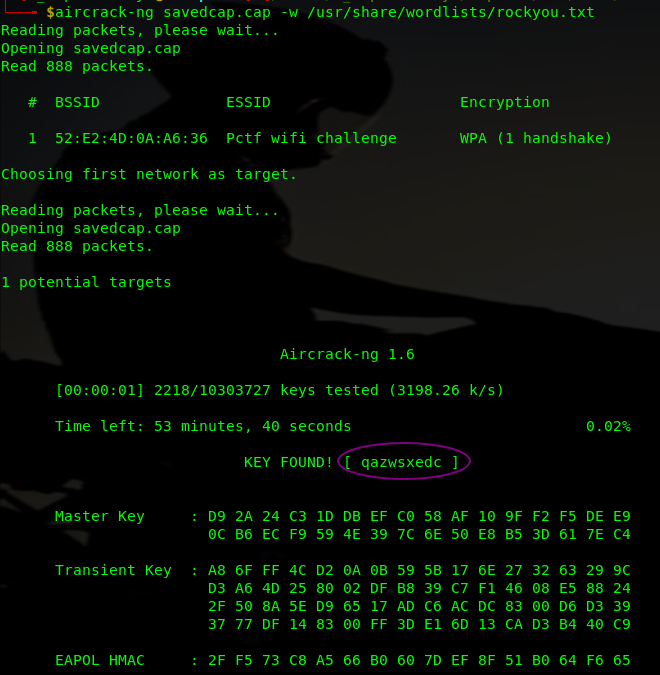
a. WPA
We are given a pcap file which seems to have a 4 way wifi handshake. Let’s proceed to decipher the wifi keys with aircrack-ng.
That was first!
PCTF{qazwsxedc}
b. Twins
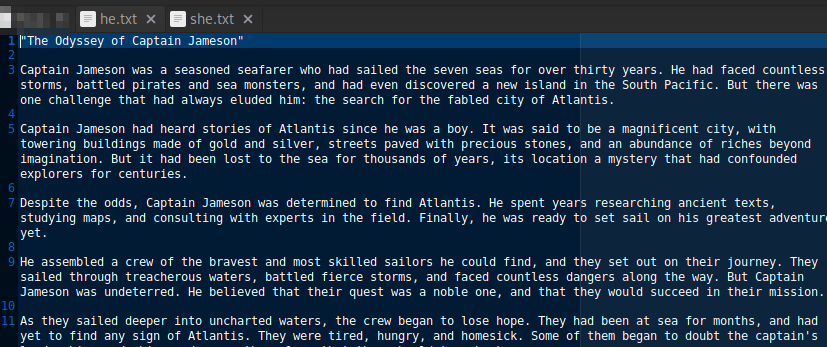
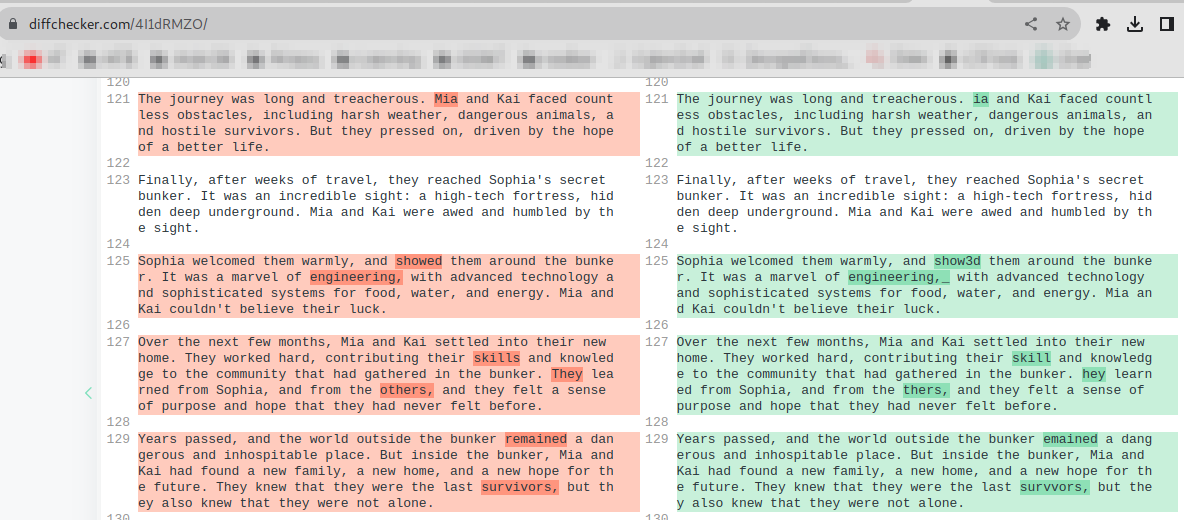
We are give two files: he.txt and she.txt. They seem to have the same content but diff showed some difference.
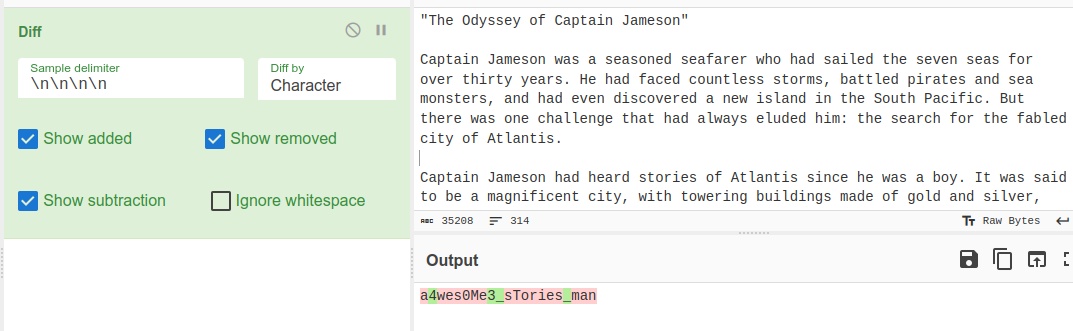
I uploaded to diff checker and checked out the differences.
I wrote down the unique characters from the highlighted words to get the flag. Alternatively, pasting both file contents in cyberchef and separating them by 4 lines gives the flag faster.
PCTF{4wes0M3_sTories_man}
I had fun solving these and more challenges from the many challenges in PatriotCTF2023. As I was learning I explored several ways of solving them.
There are many ways of killing a rat! Till next time.
Happy Hacking.