Let’s take a look at some ctf challenges from the bootcamp. Bootcamp Link
Challenge 1: mask(Network Security Fundamentals)
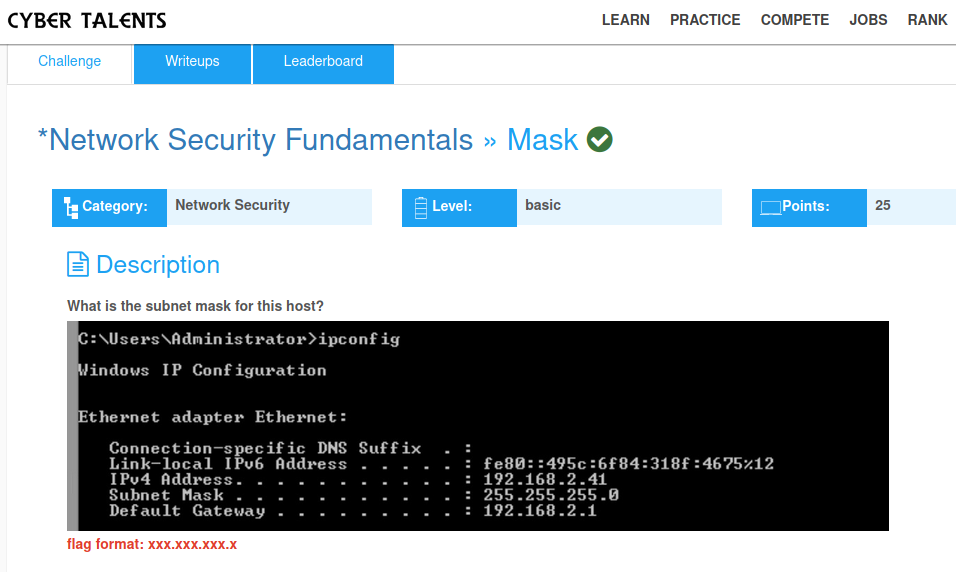
What is the subnet mask for this host?
flag format: xxx.xxx.xxx.x
*Description **In Windows, **ipconfig* **is a console application designed to run from the Windows command prompt. This utility allows you to get the IP address information of a windows computer. It also allows some control over your network adapters, IP addresses (DHCP-assigned specifically), even your DNS cache. From the terminal we can see the subnet mask of the computer.
Solution
255.255.255.0
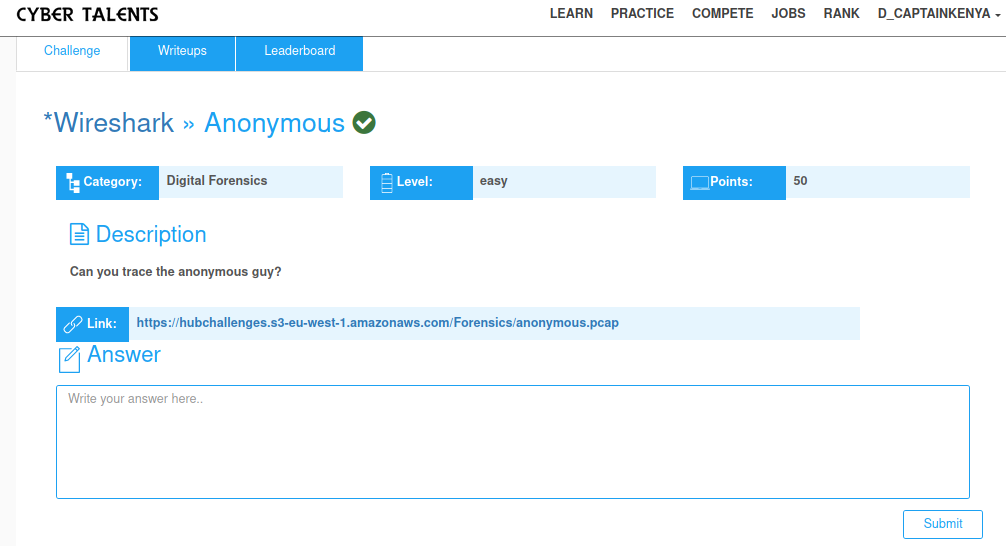
Challenge 2: anonymous(Wireshark)
Can you trace the anonymous guy?
Solution
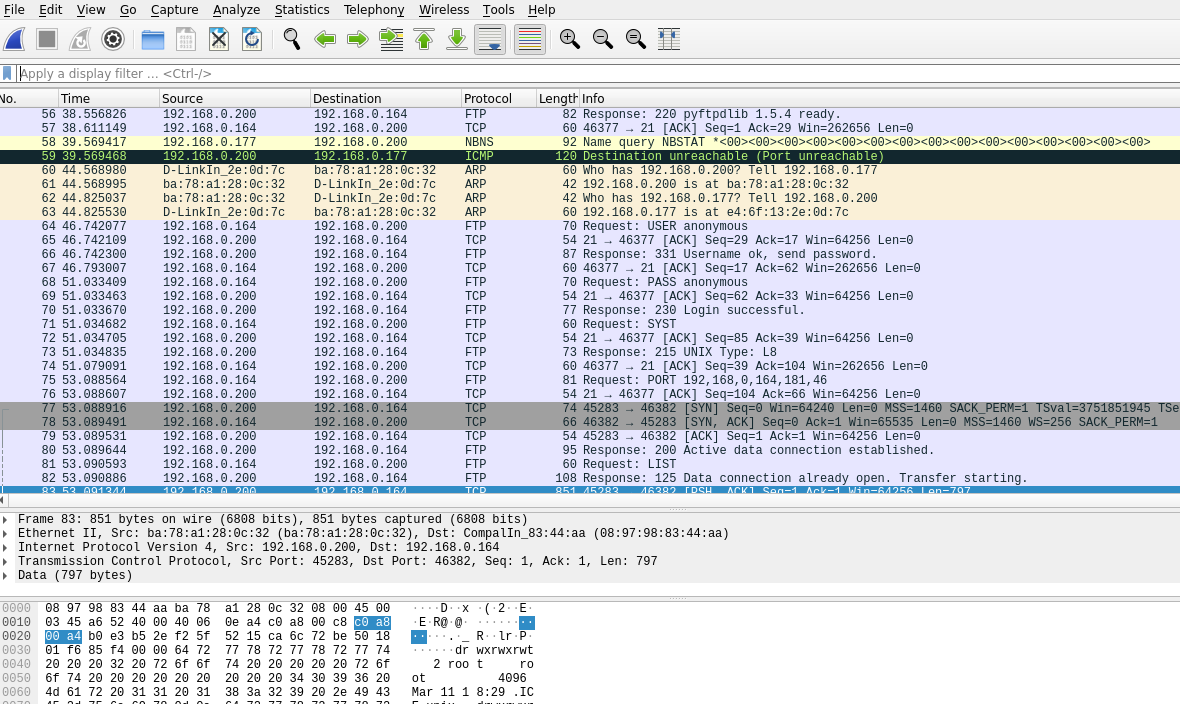
Go ahead and download the ‘pcap’ file from the description link. Open the file with Wireshark.
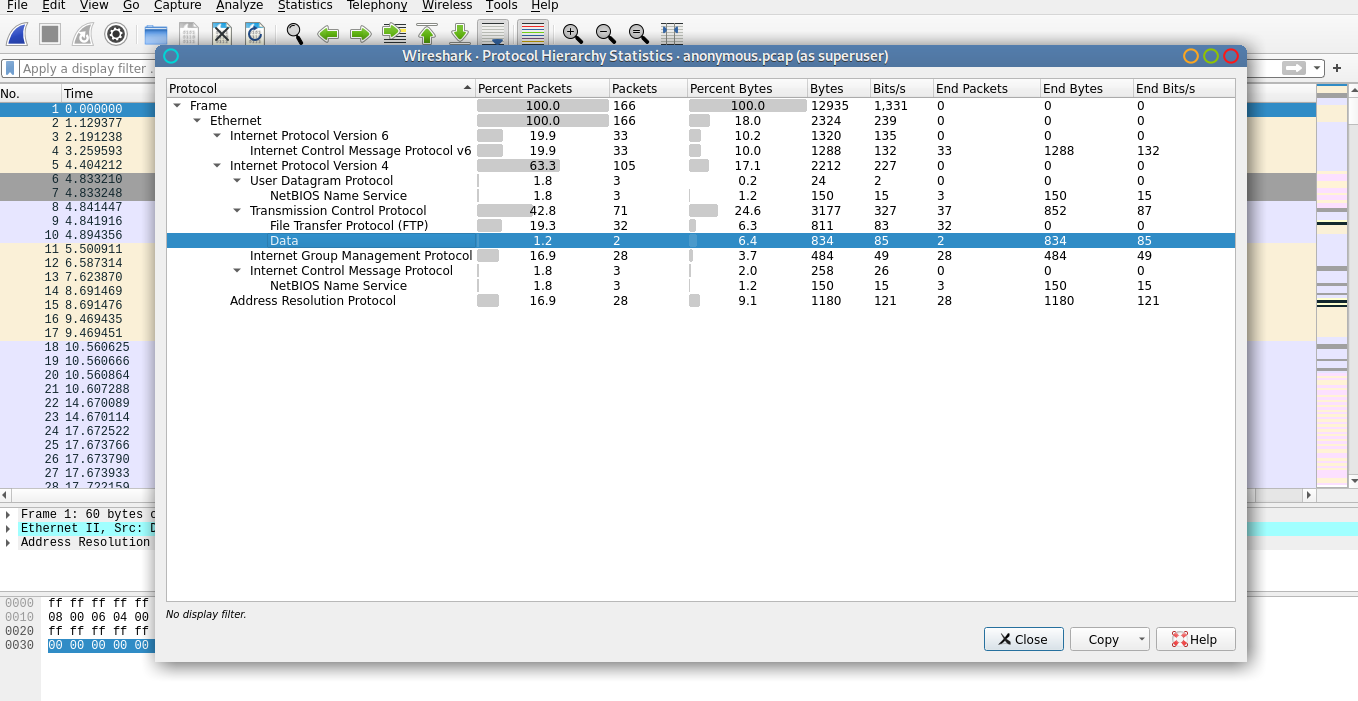
From tabs(top), go to Statistics, Protocol Hierarchy.
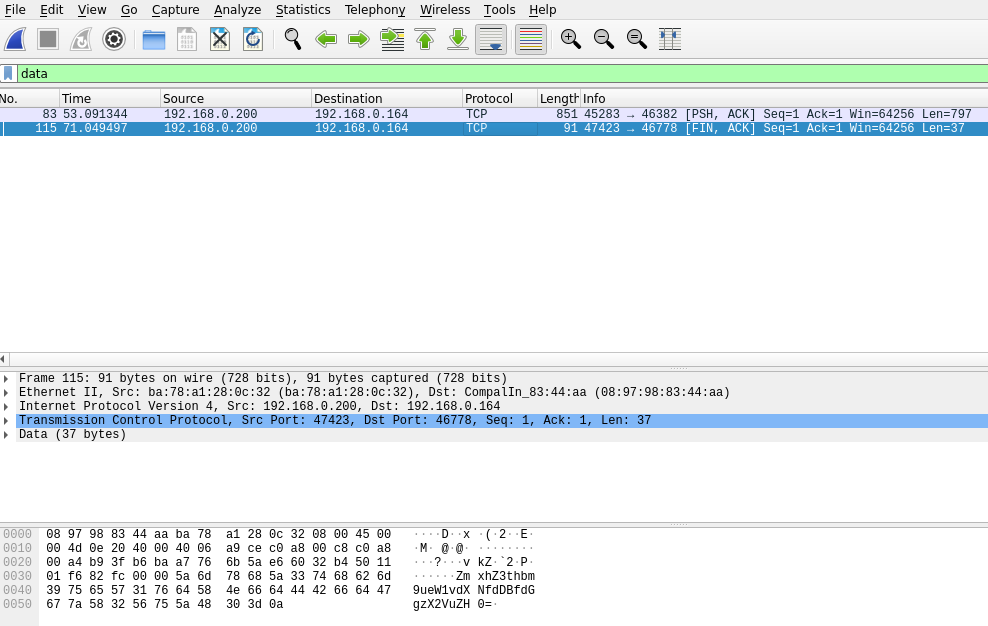
Right click on ‘Data’ and select ‘apply as filter’, ‘selected’
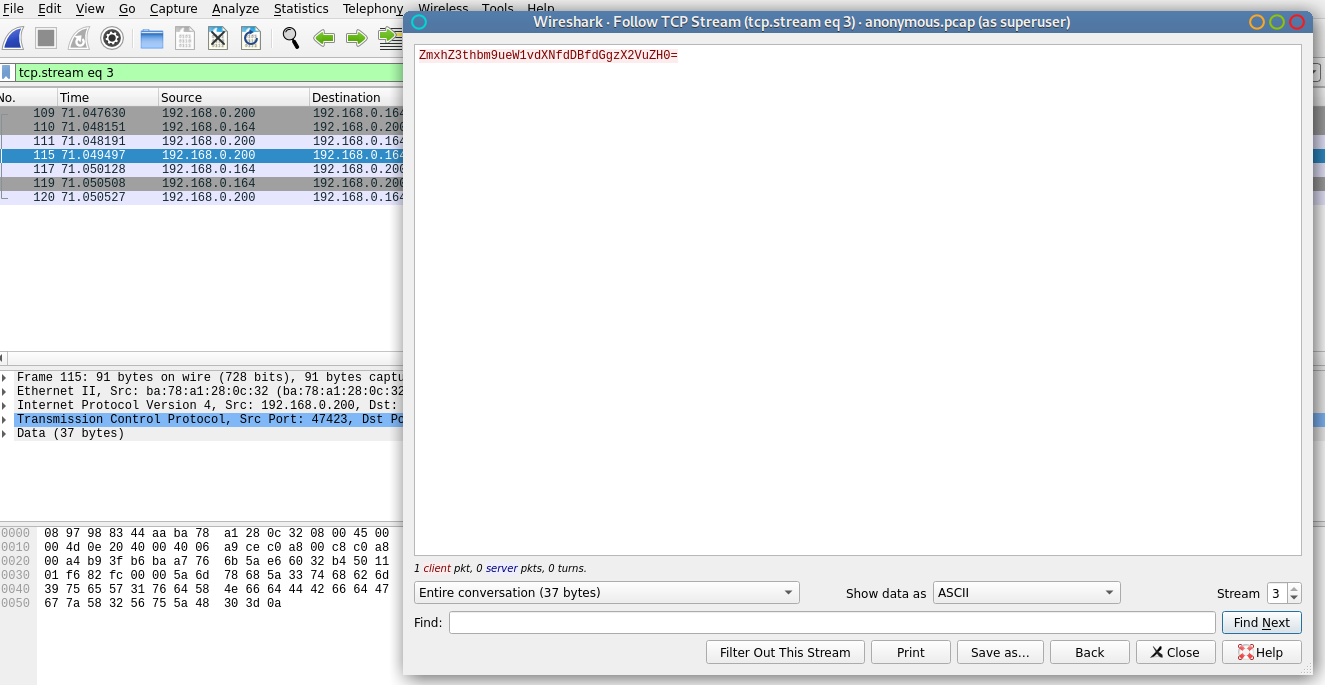
Right click on second packet and ‘Follow’, ‘TCP stream”
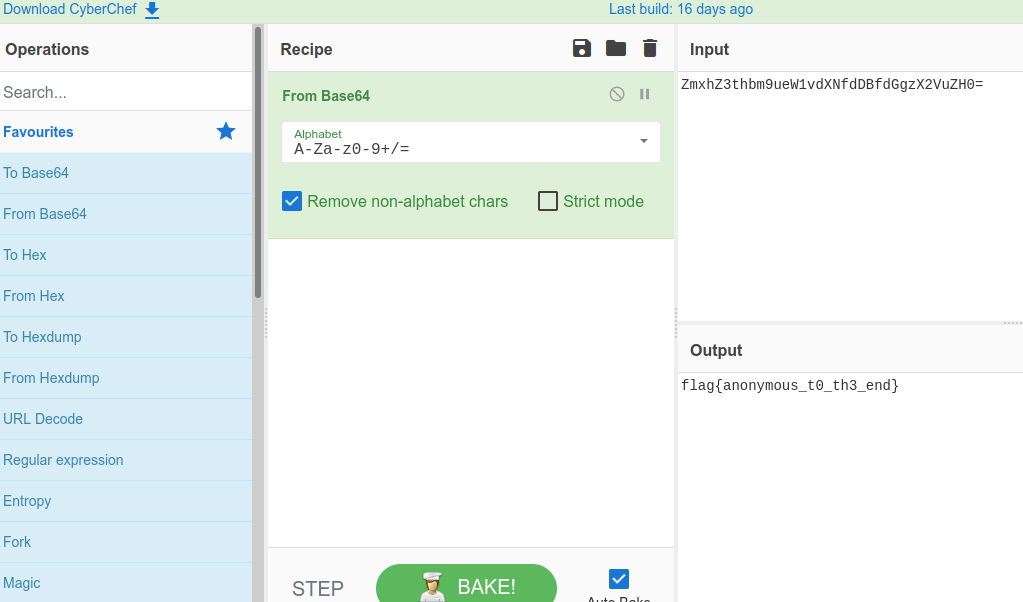
Decode the string that appears from base64. I really like CyberChef.
And somehow you have your anonymous flag.
Challenge 3: Hide data(Data Encryption)
Description
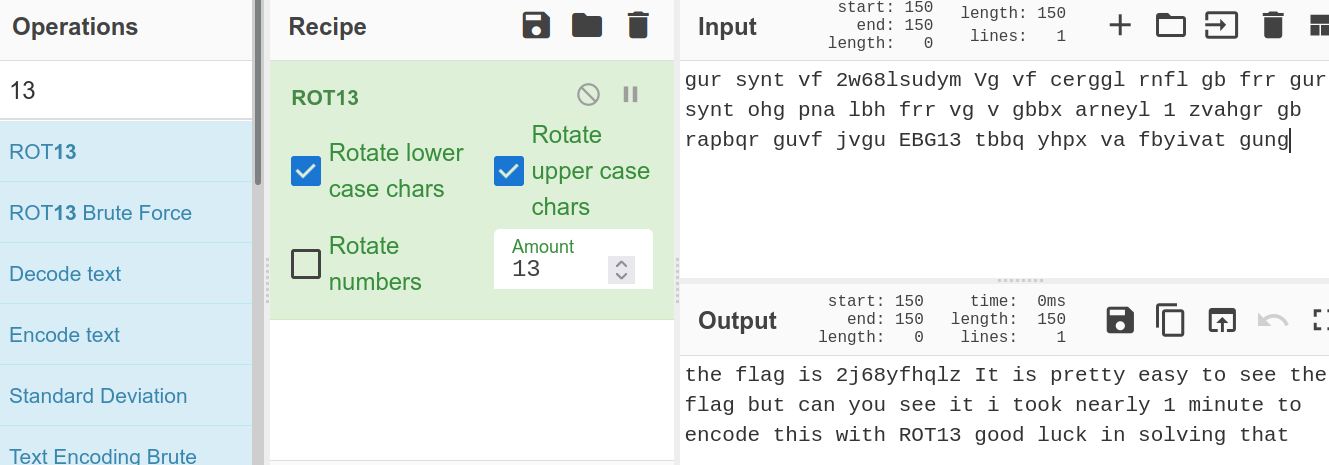
I used to hide my data with a classic cypher, can you get the flag hidden inside? gur synt vf 2w68lsudym Vg vf cerggl rnfl gb frr gur synt ohg pna lbh frr vg v gbbx arneyl 1 zvahgr gb rapbqr guvf jvgu EBG13 tbbq yhpx va fbyivat gung
Solution
Copy paste the string into cyberchef. Use ROT13 recipe and bake for this delicious flag.
And there you have your flag.
Challenge 4: Keep ASCIIng(Data Encoding)
Description
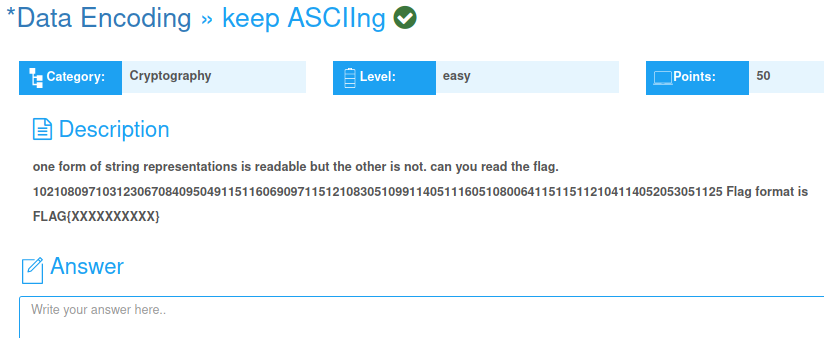
One form of string representations is readable but the other is not. can you read the flag. 102108097103123067084095049115116069097115121083051099114051116051080064115115112104114052053051125 Flag format is FLAG{XXXXXXXXXX}
Solution
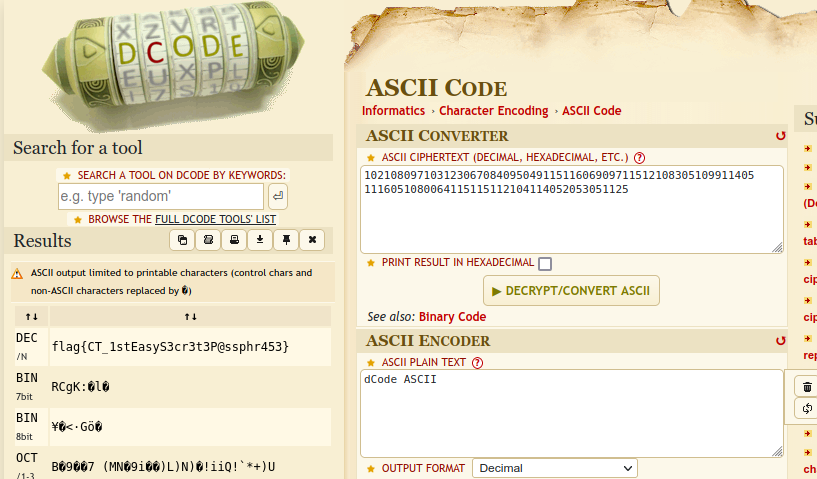
For ASCII I simply went HERE
And there we go, our flag is right there, not on the right though.
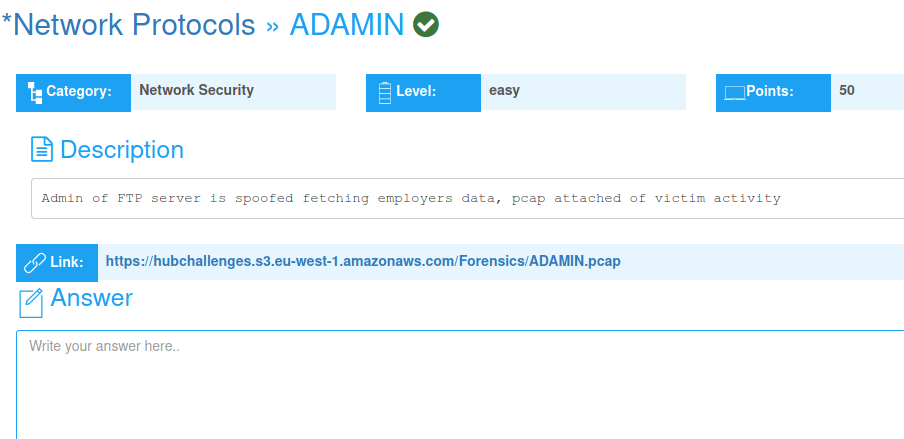
Challenge 5: ADAMIN(Network Protocols)
Description
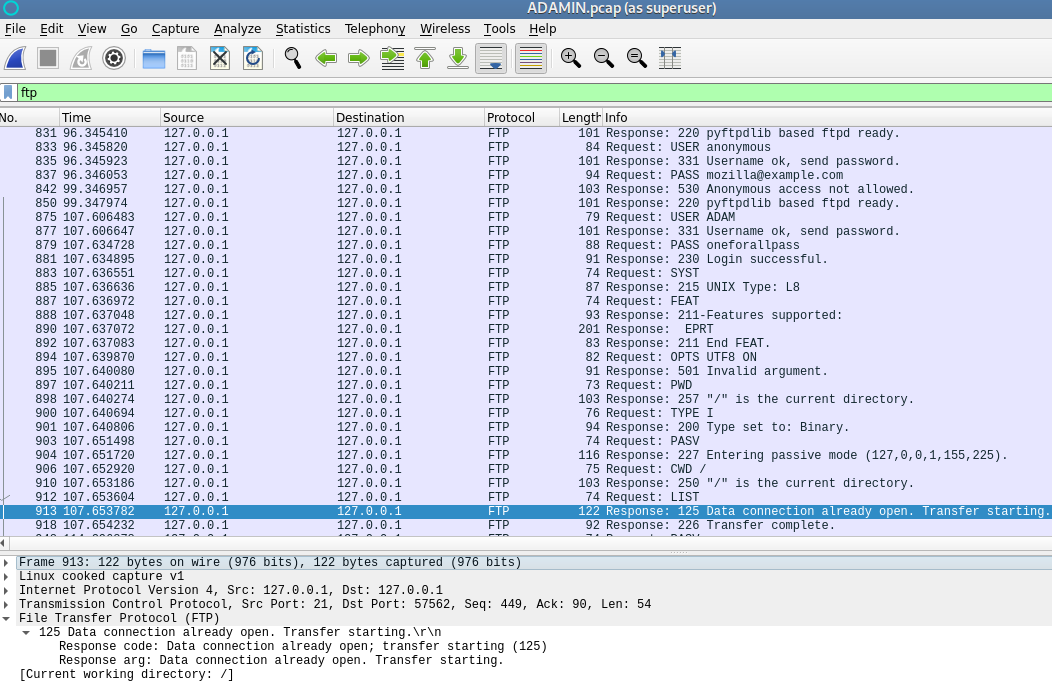
Download the pcap file and open it with wireshark. I looked at the udp packets but nothing cool about them stuff is in ftp. Filter the packets to ftp and follow along.
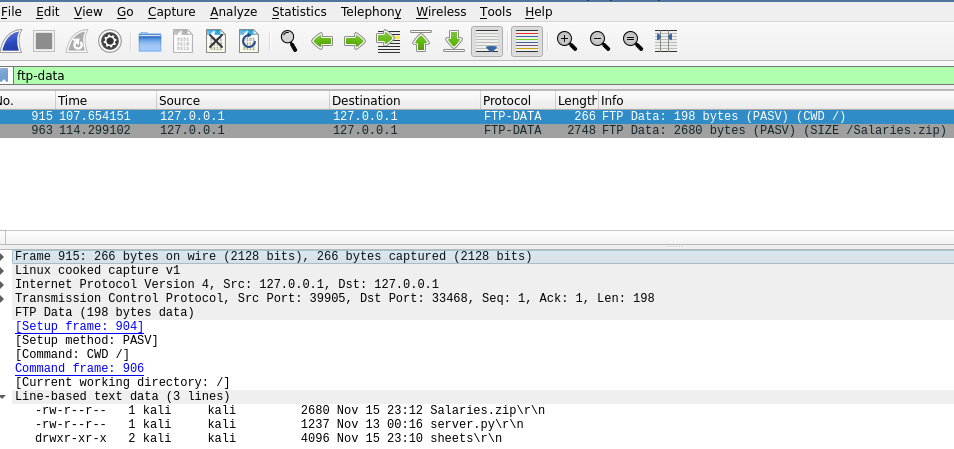
You have seen packets 875 and 879. They give use a username: ADAM and a password: oneforallpass, try not to forget what you see. Let’s check for some data through the ftp. Filter the packets further with “ftp-data”
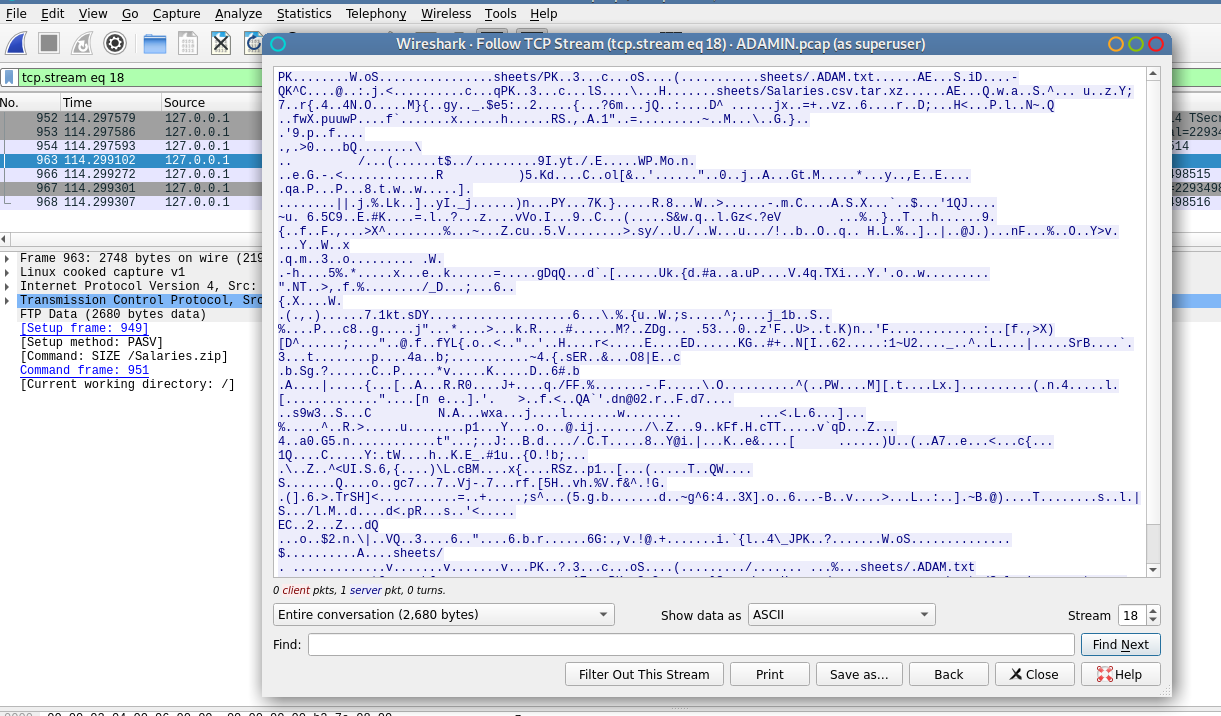
Interesting. Let’s check the packet with some zip file and follow it’s tcp stream.
Change the ASCII data(show data as) into raw and save it(save as). Now extract the zip file you saved.
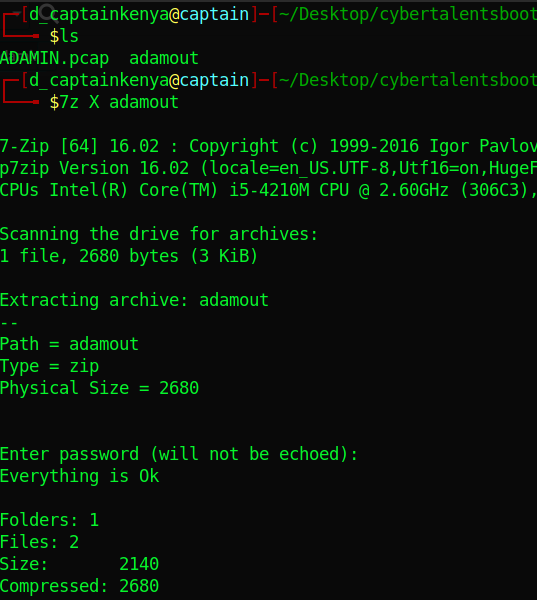
tar will do or use ‘7z x zipfilename’ if you have 7z. When prompted for a password remember to remember what you saw earlier.
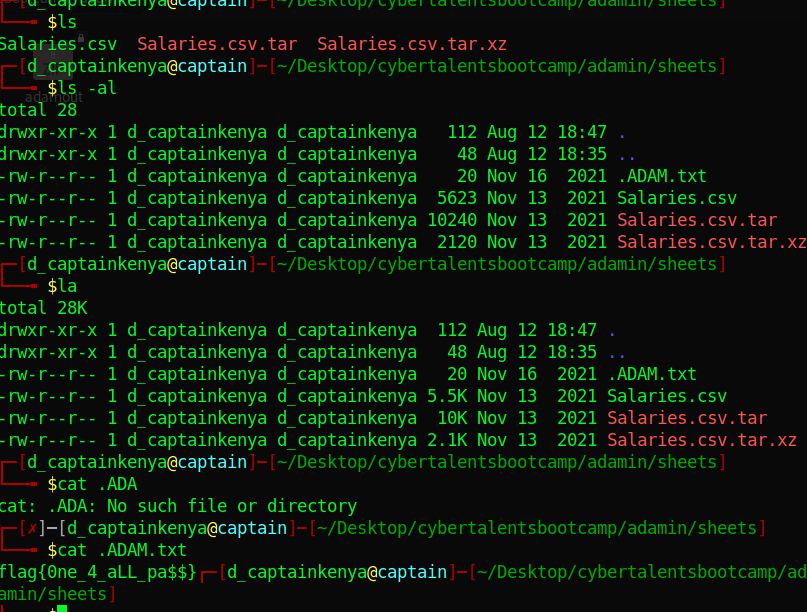
Listing the directory shows a ‘sheets’ directory, heading there we find another compressed file.
Let’s decompress it with: 7z X Salaries.csv.tar.xz We get Salaries.csv.tar Let’s decompress it again: 7z X Salaries.csv.tar
Listing the directory we see a ‘salaries.csv’ file which doesn’t seem to have any flag. List the directory once more and this time with ‘ls -al’ ‘la’ does it for me too.
Notice and open that hidden txt file over there and get your flag.
Solution
flag{ follow along }
Challenge 6: This is Sparta(Javascript)
Description
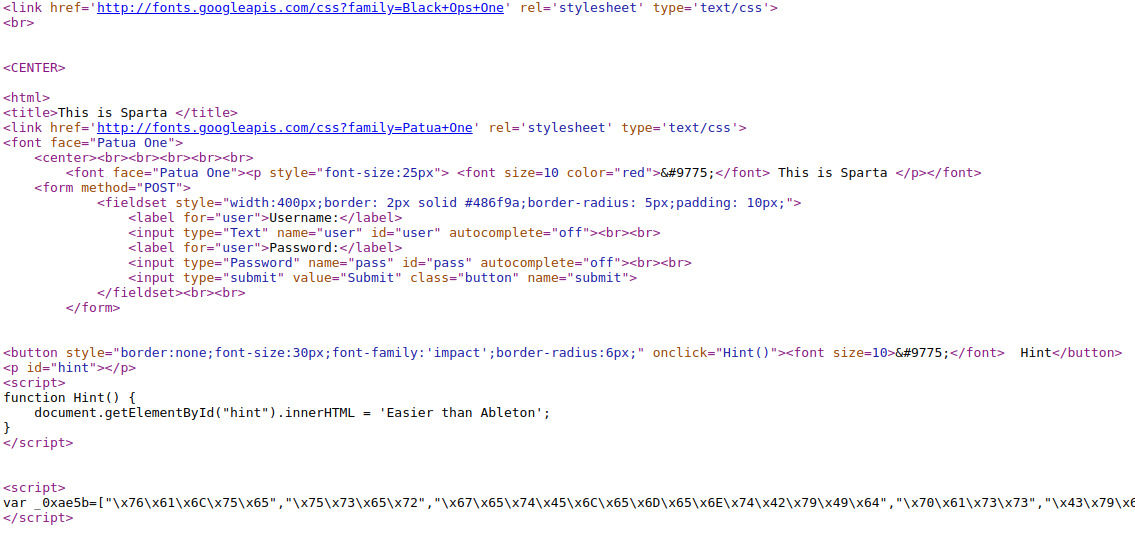
Starting the challenge we head to a login page. The hint seems to just encourage us. Let us view the page source.
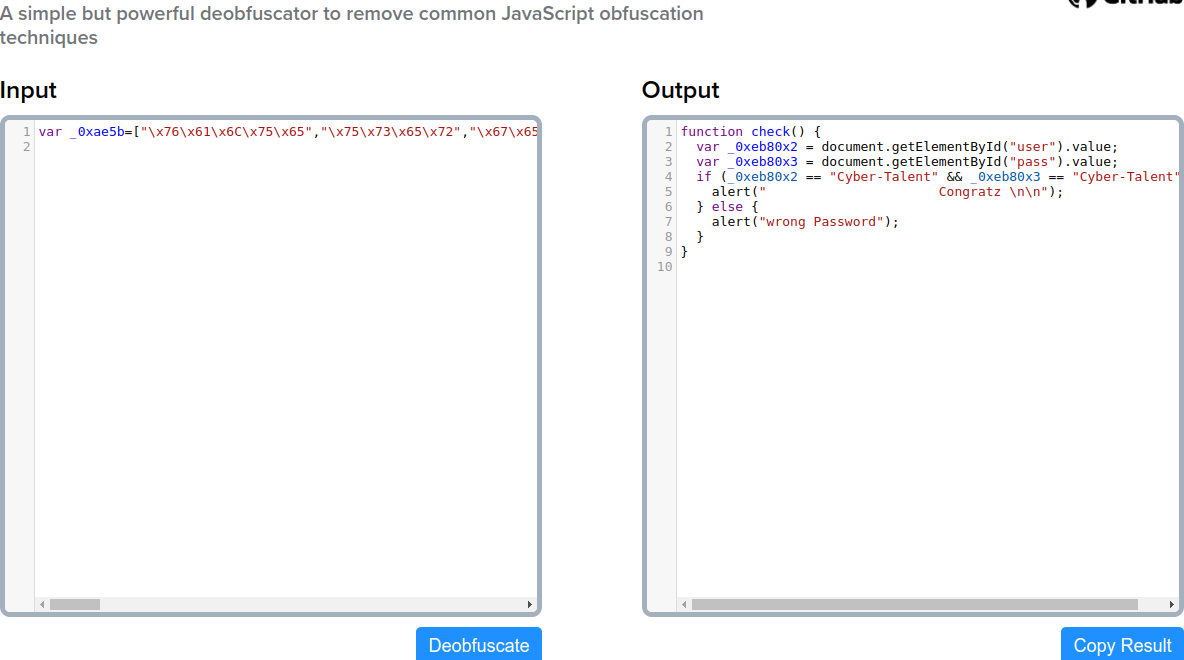
We see some weird(obfuscated) javascript down there. Copy the code in between the script tags and paste it here as the input. Let us deobfuscate it.
Inspecting the output we can clearly see that the Js code is checking if the username and password entered is ‘Cyber-Talent’ before granting access. Let’s go ahead and login.
On logging in we get our flag.
Solution
Where the curly braces begin.
Challenge 7: Admin has the power(Cookies)
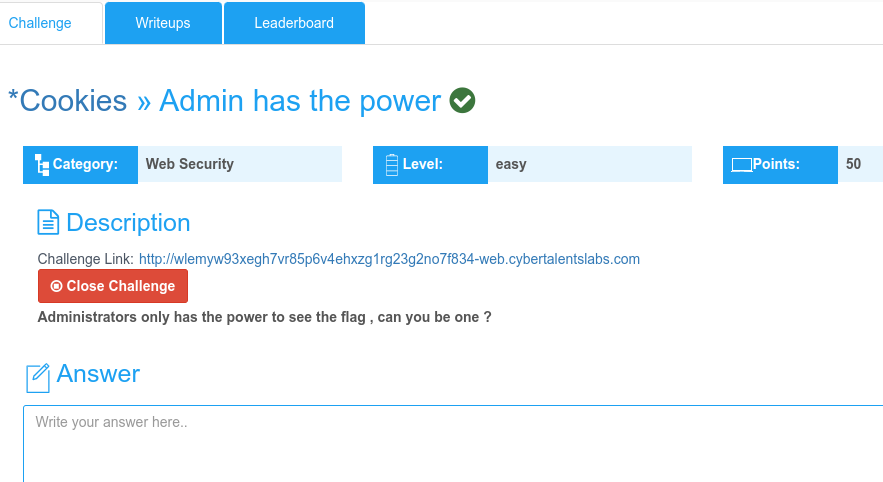
Description
Starting the challenge we are redirected to a login page
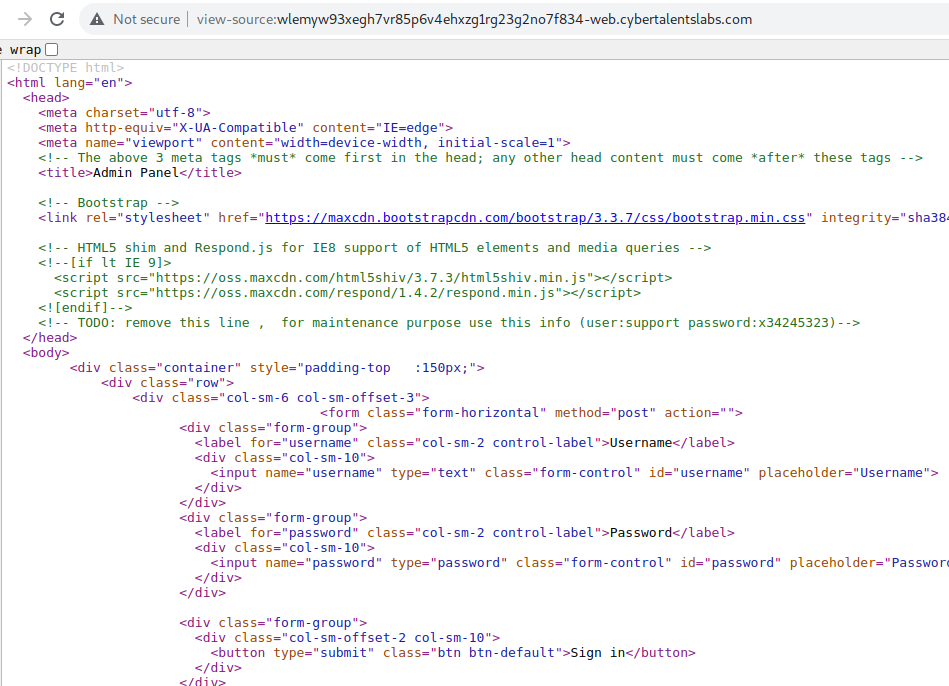
Let’s see the page source for this page.
Nice, The developer left some credentials for maintenance purpose. Log in using those creds.
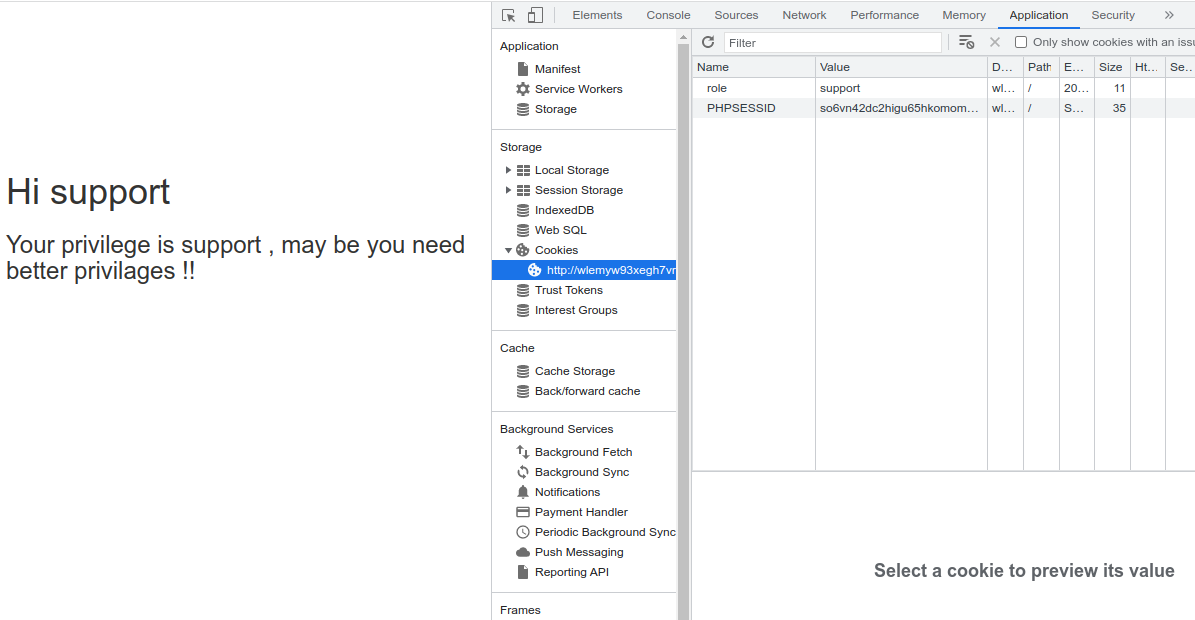
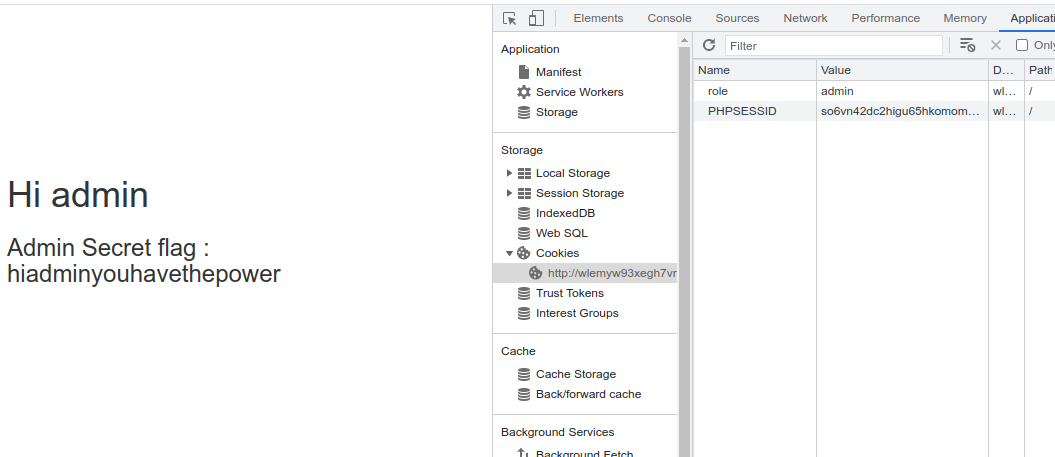
The site welcomes us as support but we really need the powers of the admin. Looking at the cookies, we have a cookie named ‘role’ with a value ‘support’. Let’s change the value to ‘admin’ and refresh the site.
Solution
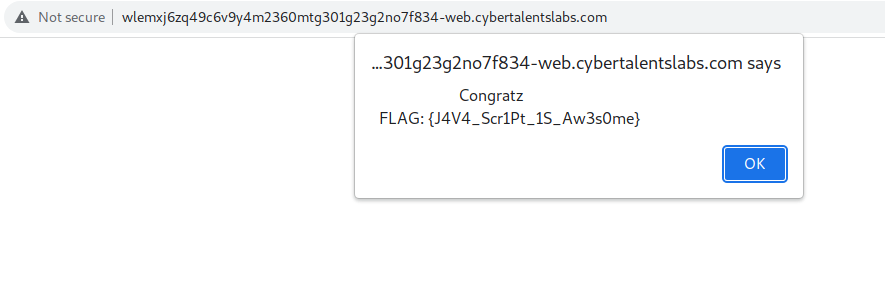
Refreshing the site we are given the power to see the flag.
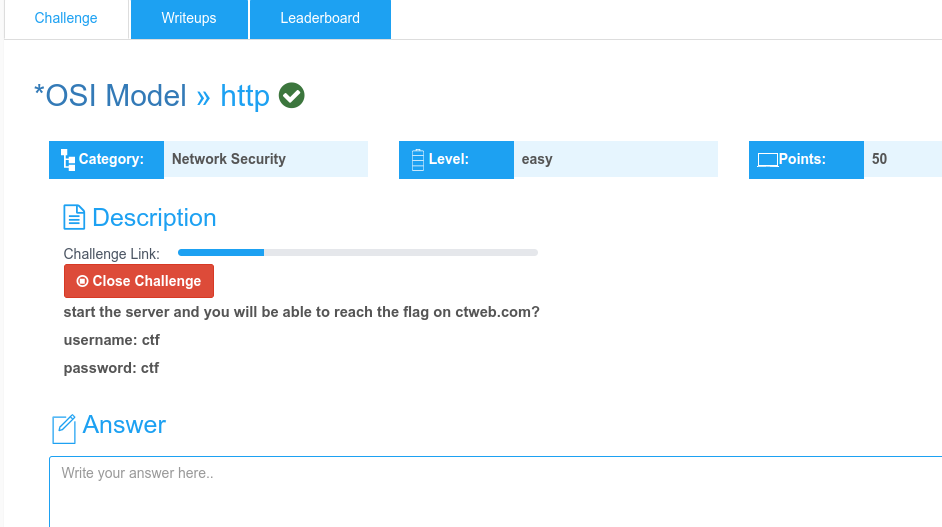
Challenge 8: http(OSI Model)
Description
Start the server and login.
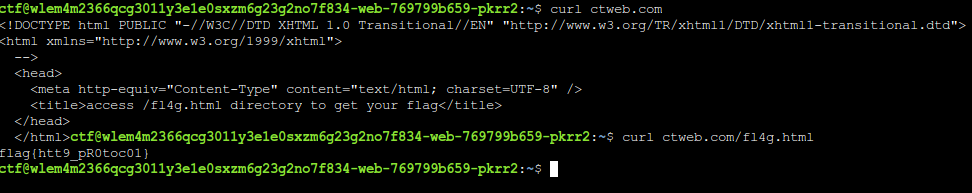
Use curl on ctweb.com
Solution
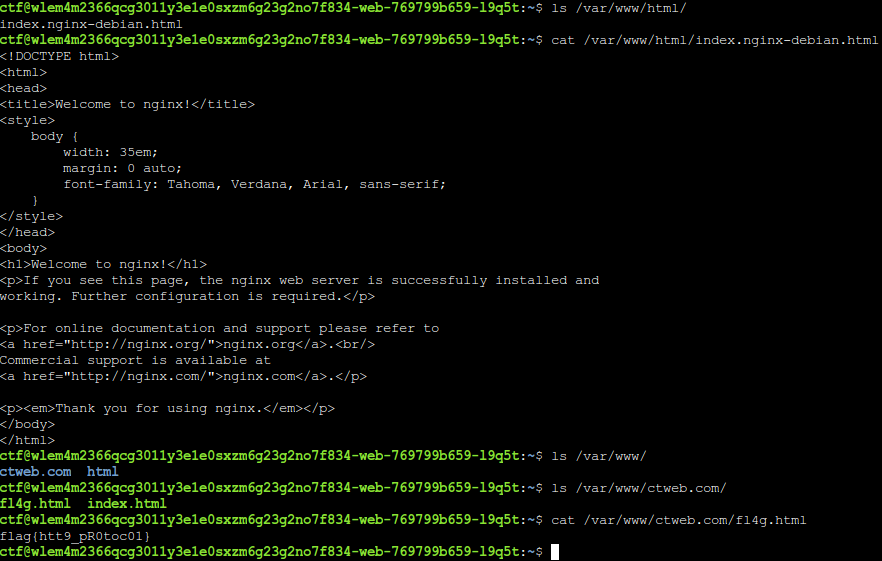
Going through the html response, we have a fl4g.html describe at the title tags. Curl through the page and get your flag.
You could also check the root directory on the server as follows.
Challenge 8: I love music(Steganography)
Description
Download the wav file and open it with audacity. If you don’t have it installed run ‘sudo apt update’ and sudo apt install audacity’
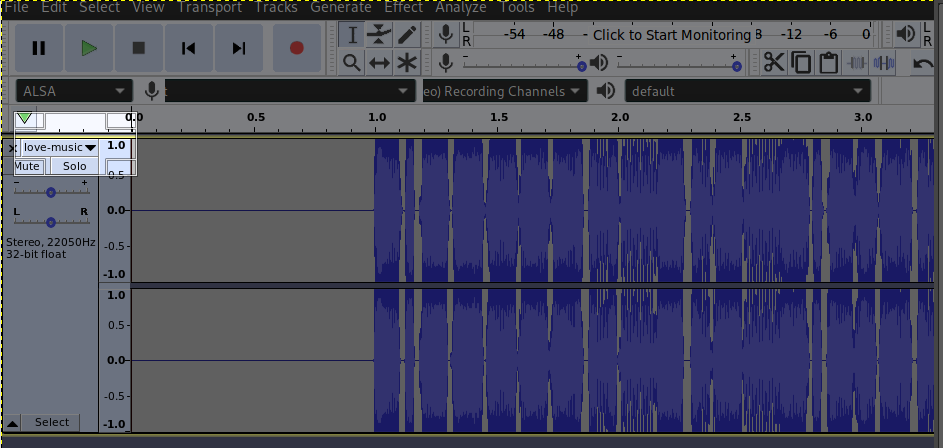
Change the view to ‘spectogram’ from the highlighted section.
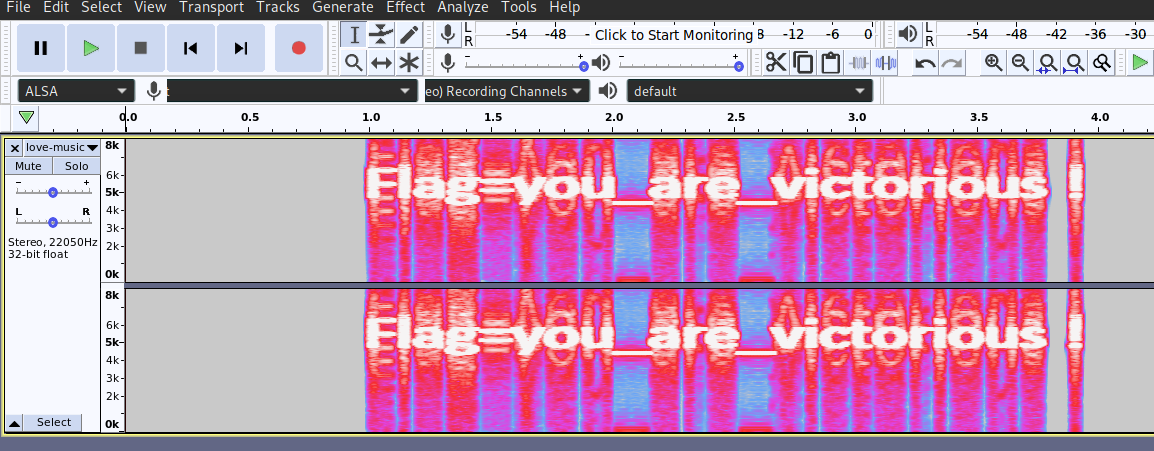
Solution
There you go.
Challenge 9: Images3c(Steganography)
Description
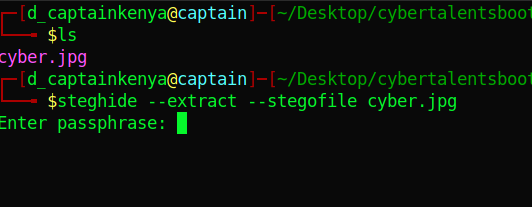
I checked the image with exiftool and found nothing. I tried extracting hidden files with steghide which prompted for a passphrase.
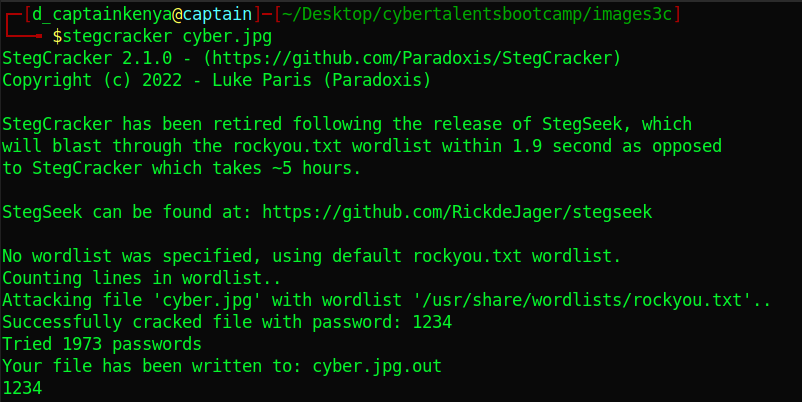
Let’s crack the passphrase with stegcracker.
Solution
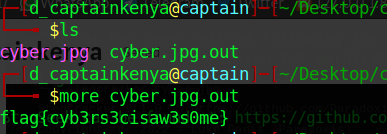
We have a cyber.jpg.out file let’s check on it.
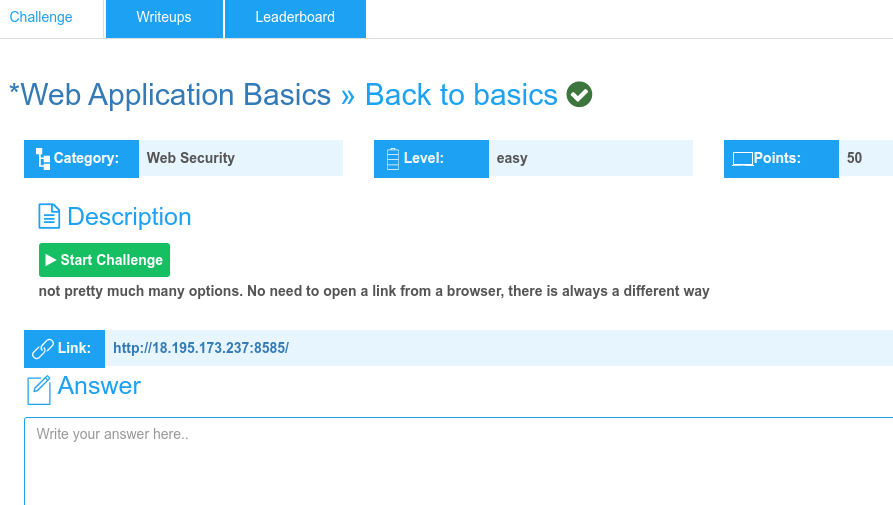
Challenge 10: Back to basics(Web Application Basics)
Description
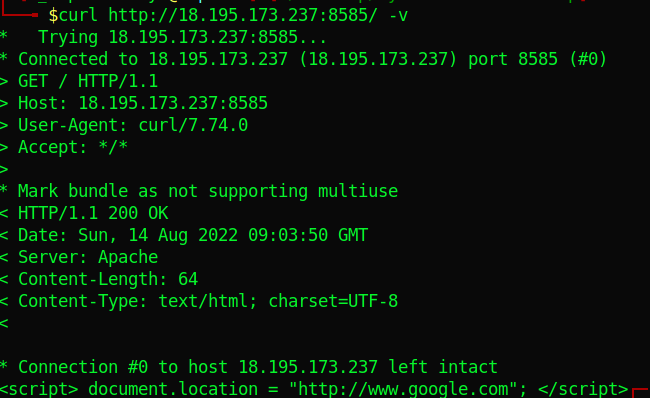
Tried curl on the link but got nothing.
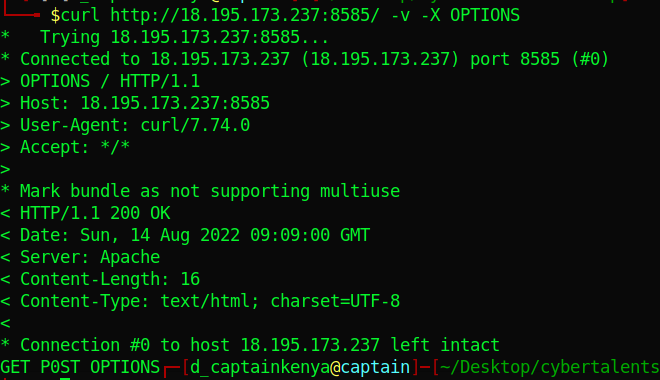
Different servers can have custom methods apart from the usual: GET, POST, PUT, DELETE etc. Let us see what this one supports.
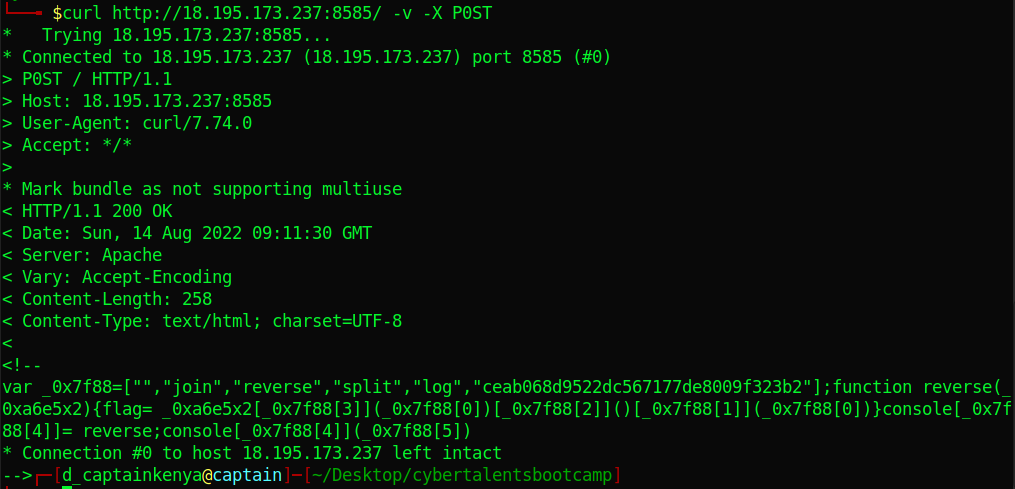
Down there we see the available options. Using GET gives us nothing. Let us use P0ST. Notice the 0 and not O.
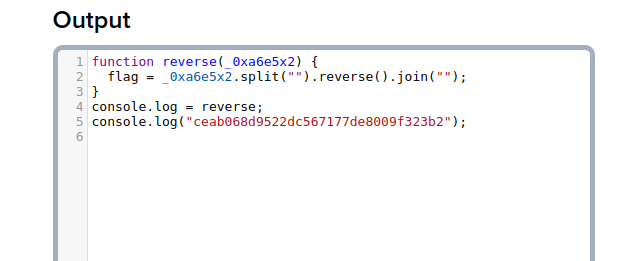
Notice the extra output. Looks like some obfuscated Javascript. Let’s deobfuscate it here.
Here is our flag but it seems to be reversed by the Js function.
Solution
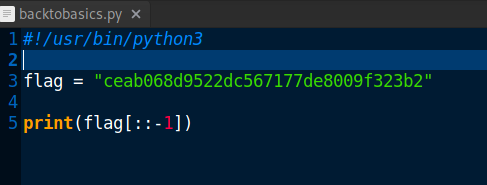
Let us reverse it to the original flag with some python.(You can use any other means.)
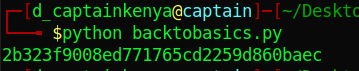
Save as python file and execute it to get original flag.
Challenge 11: Cheers(PHP Basics)
Description
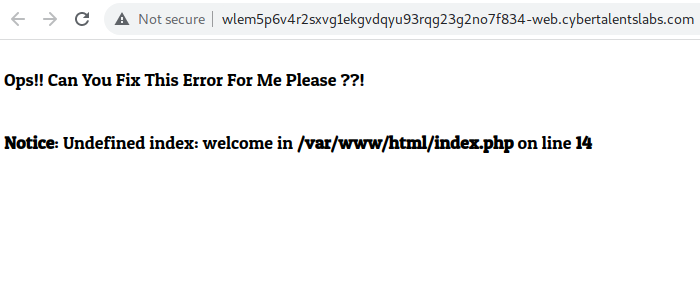
Starting the challenge leads us to a broken index page.
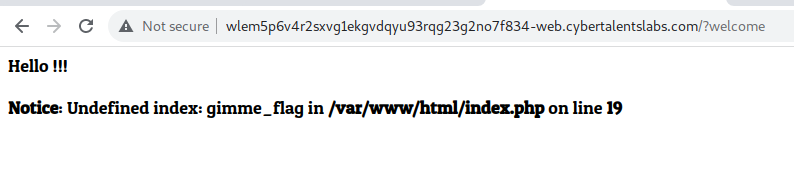
I tried ‘flag.txt, flag.php and /welcome.php’ end points but got 404s. I tried ‘/?welcome’ and got some cool response.
Solution
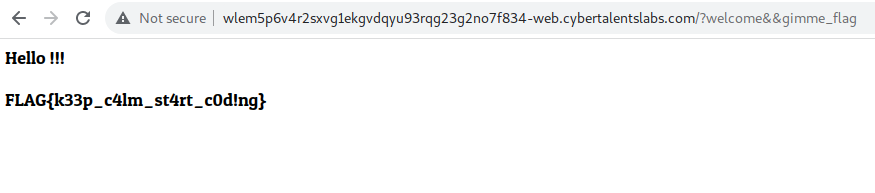
I tried ‘/?gimme_flag’ and I was back to square one. Then I tried this ‘/?welcome&&gimme_flag’ and boom!
Nice warm up.
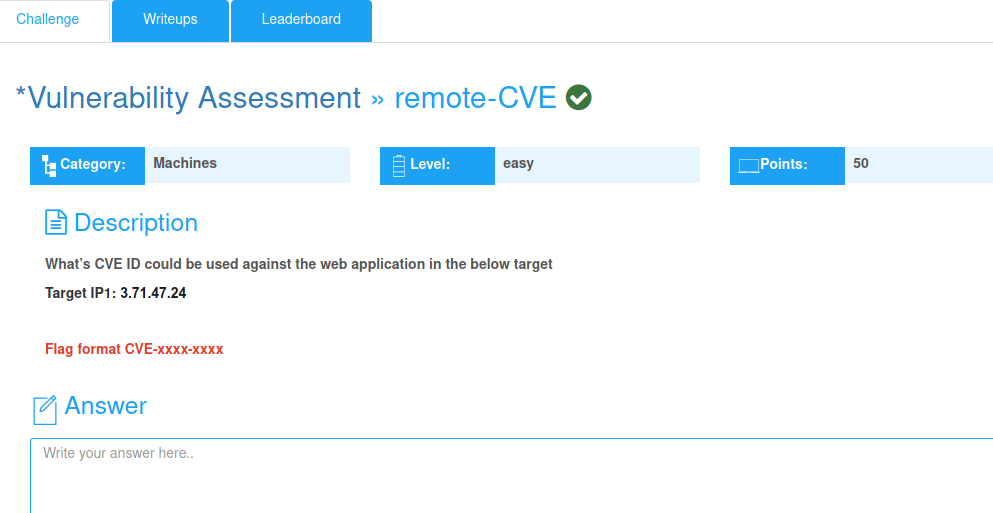
Challenge 12: remote-CVE(Vulnerability Assessment)
Solution
What’s CVE ID could be used against the web application in the below target
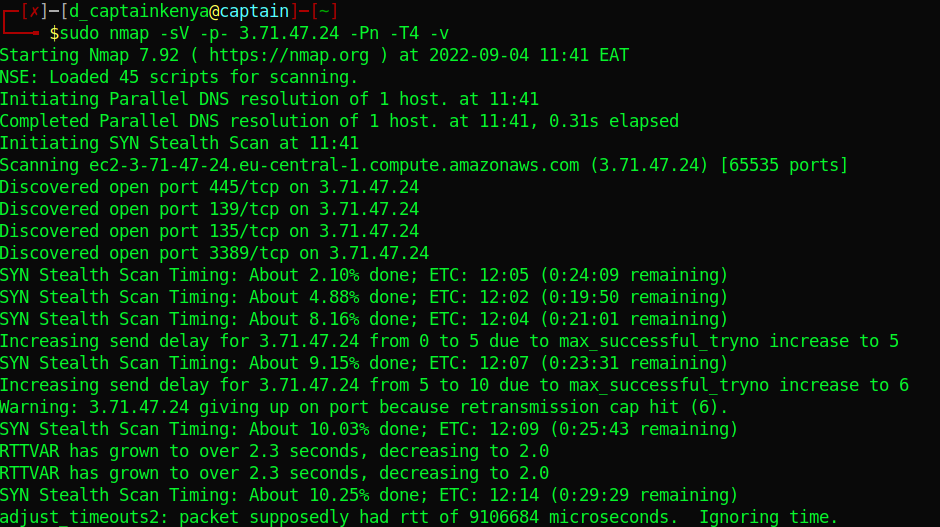
I opened the IP with Firefox but could not get a connection. I scanned the IP with nmap to check for all open ports.
| sudo nmap -sV -p- 3.71.47.24 -Pn -T4 -v |
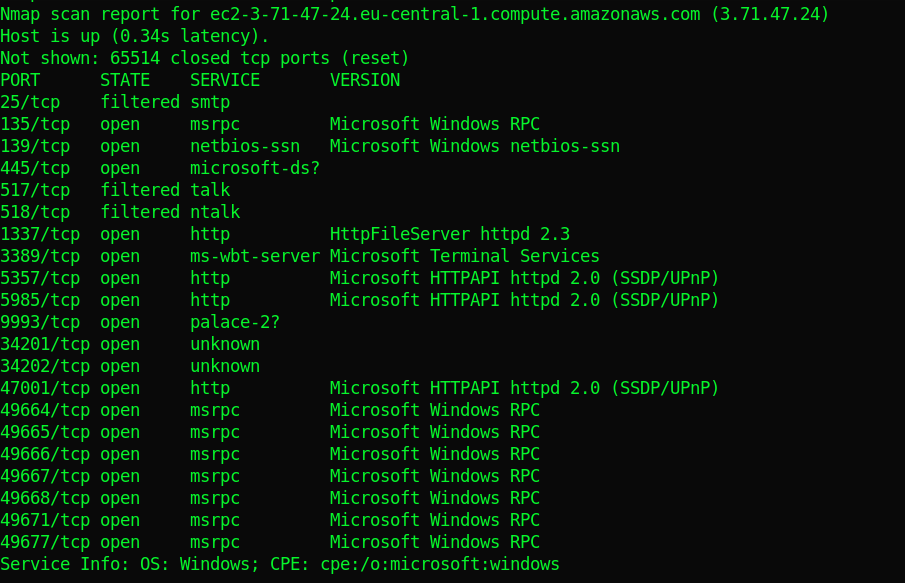
Patience pays. After a couple of seconds I got what I needed.
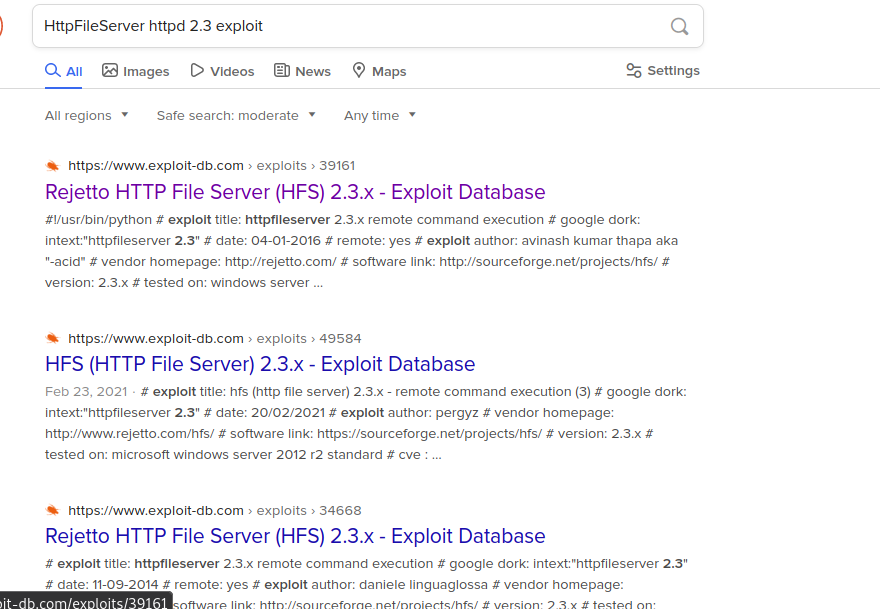
Did some googling on the first http server at port 1337: ‘HttpFileServer httpd 2.3’ and found numerous results.
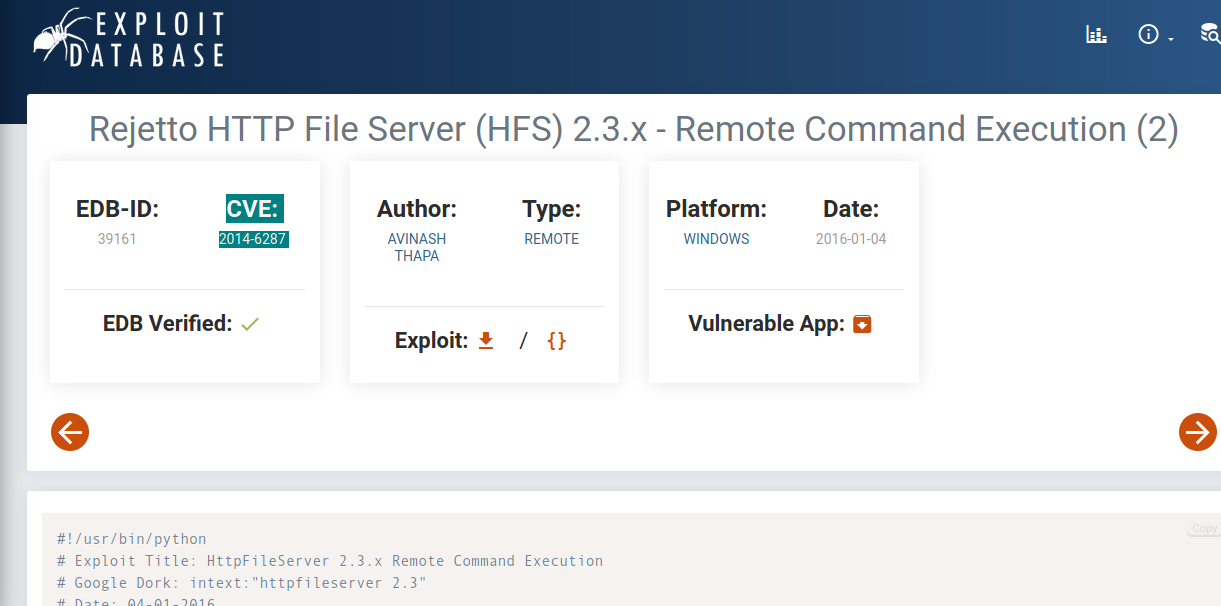
I checked out the first result.
There I got the CVE number and the vulnerability’s exploit.
Flag format CVE-xxxx-xxxx
Challenge 13: WPA Crack (WIFI Attacks)
Solution
You are conducting a WIFI pentest, Handshake has been captured and your task is to crack it
Flag format is just the password
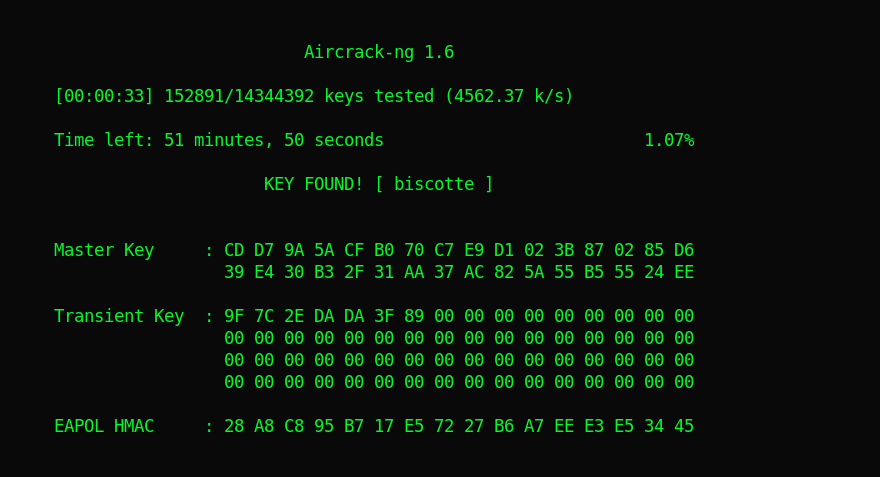
This was quit easy. I downloaded the cap file and used aircrack-ng with ‘rockyou’ for dictionary attack.
And there we got the password. This was an amazing beginner taylored bootcamp.
And by the way, There are many ways of killing a rat!
Stay Hacking.