You are involved in an incident response engagement and need to analyze an infected host using Redline.
Room link here
Difficulty: Medium
Investigating the Compromised Endpoint
Open Redline Tool and load the Mandiant analysis file into Redline. Alternatively, double click the Mandiant analysis file.
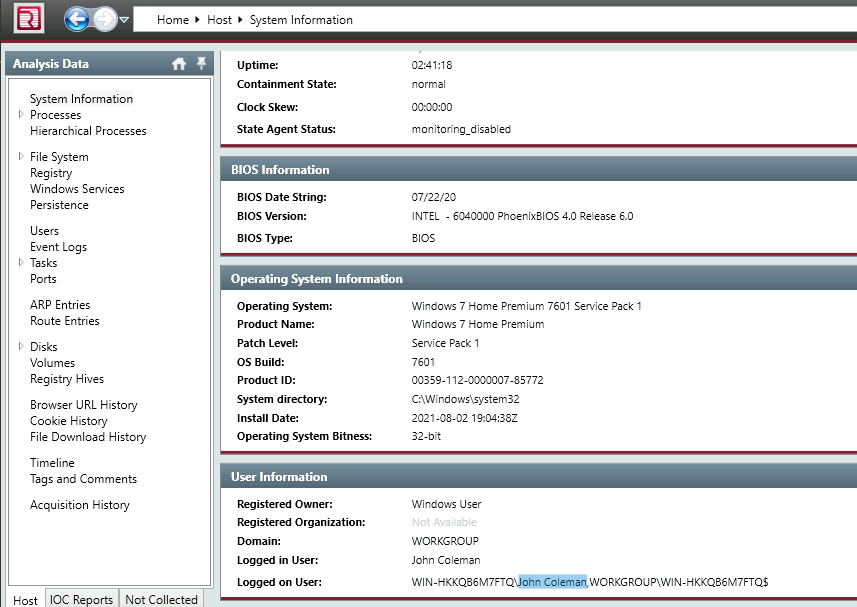
1. What is the compromised employee’s full name?
Take a look at ‘System Information’.
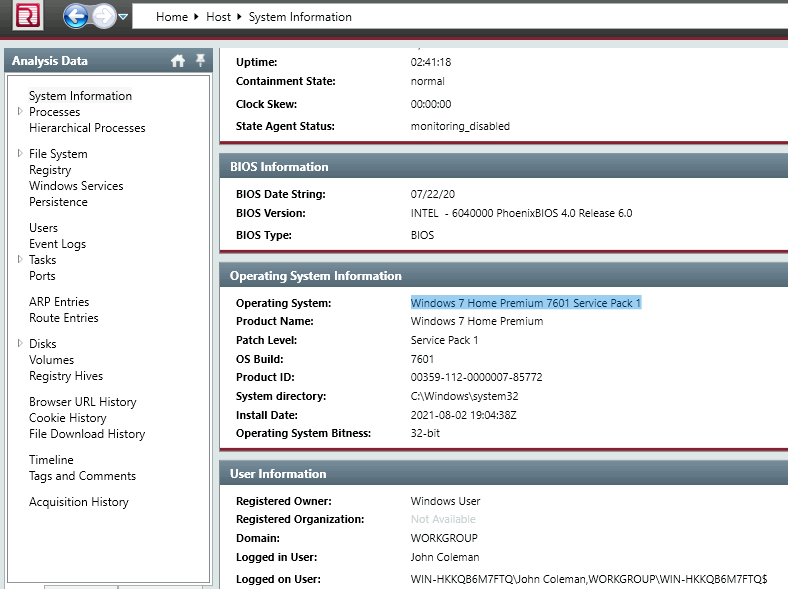
2. What is the operating system of the compromised host?
Still under ‘System Information’
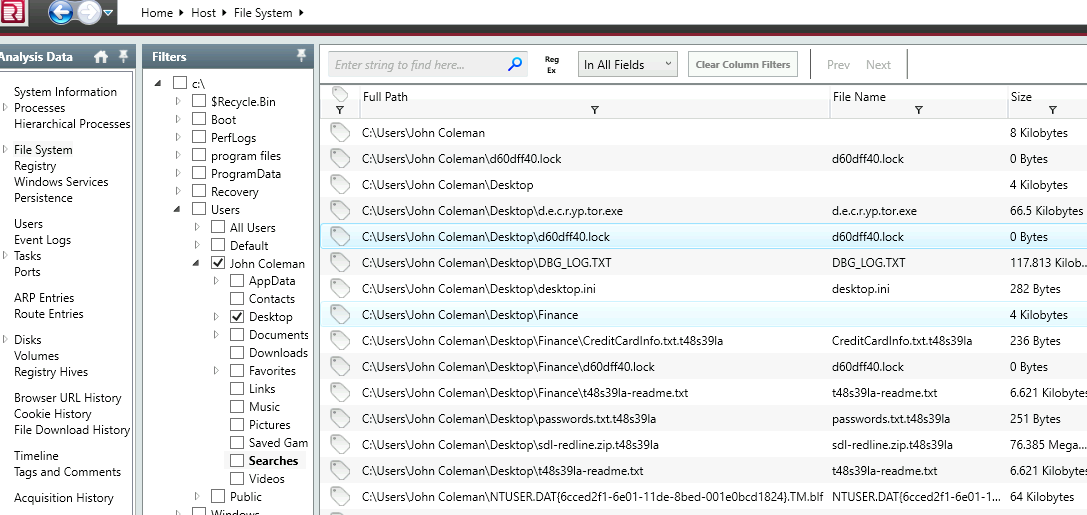
3. What is the name of the malicious executable that the user opened?
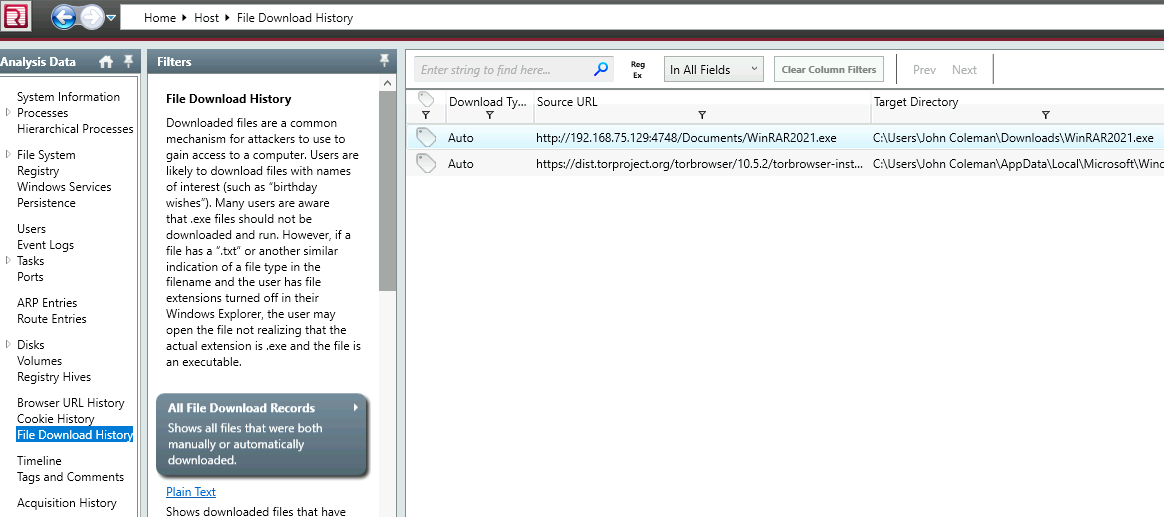
From ‘File Download History’ some file was downloaded and definitely executed.
4. What is the full URL that the user visited to download the malicious binary? (include the binary as well)
Refer image above and check ‘Source URL’
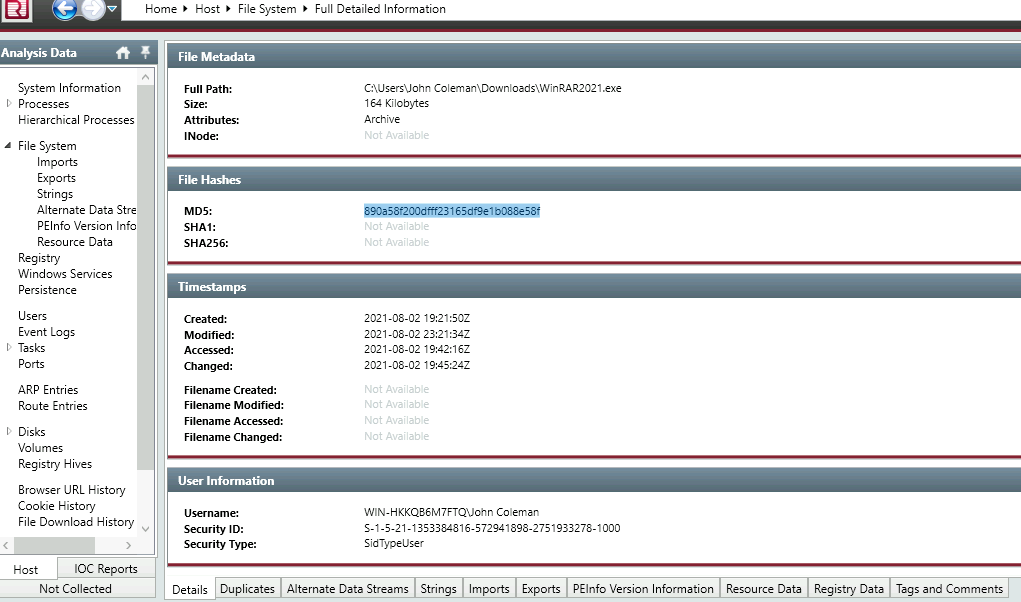
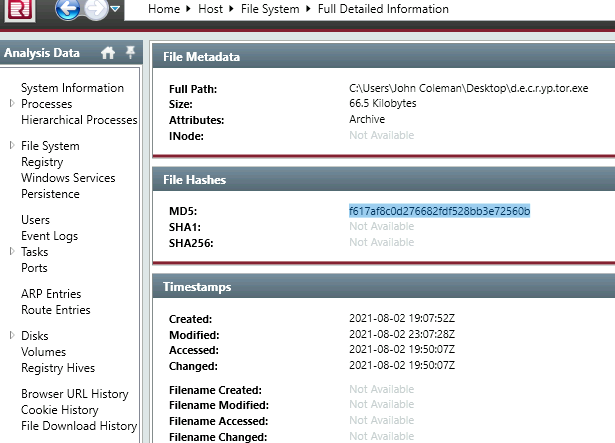
5. What is the MD5 hash of the binary?
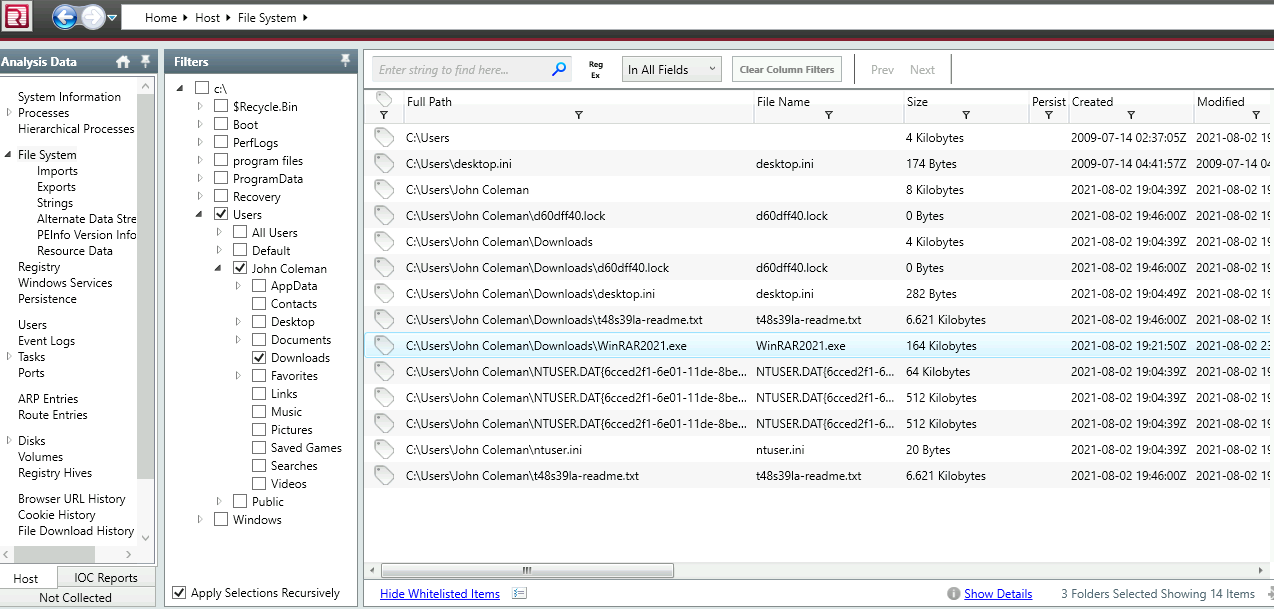
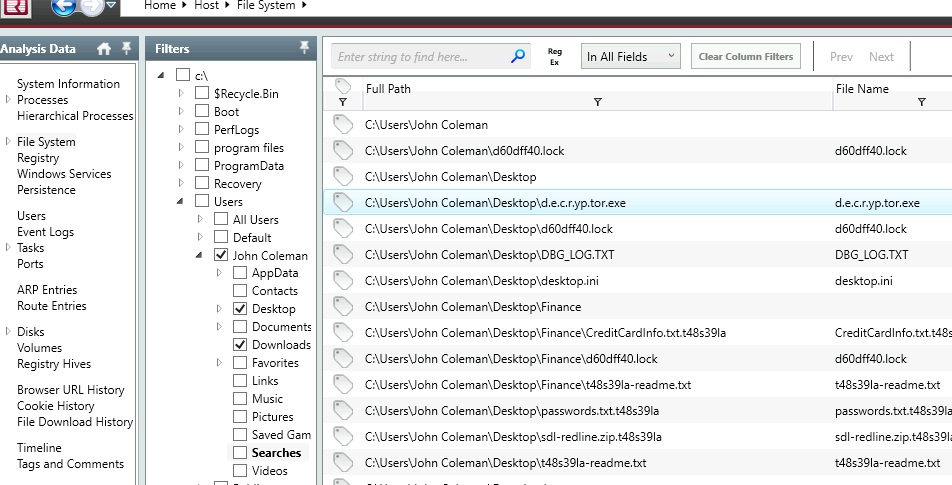
Let’s check all files from ‘File System’ Filter to only have ‘Downloads’ entries.
You can spot our malicious binary, right? Double click for more details on it.
Killed that rat!
6. What is the size of the binary in kilobytes?
It’s right up there!
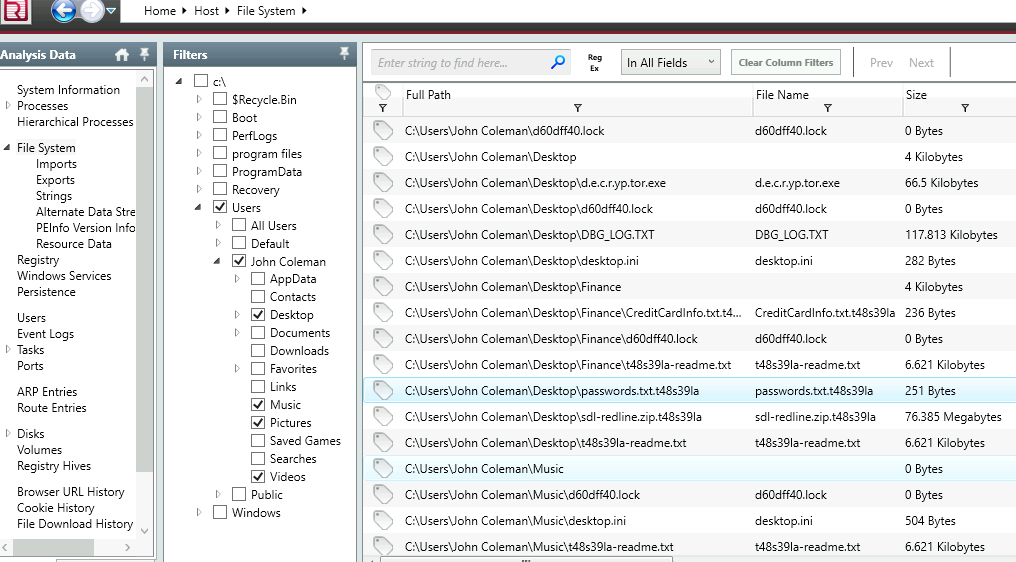
7. What is the extension to which the user’s files got renamed?
Adding more files in our filter reveals some desktop files with a weird extension.
Some weird extension name in Desktop entries.
8. What is the number of files that got renamed and changed to that extension?
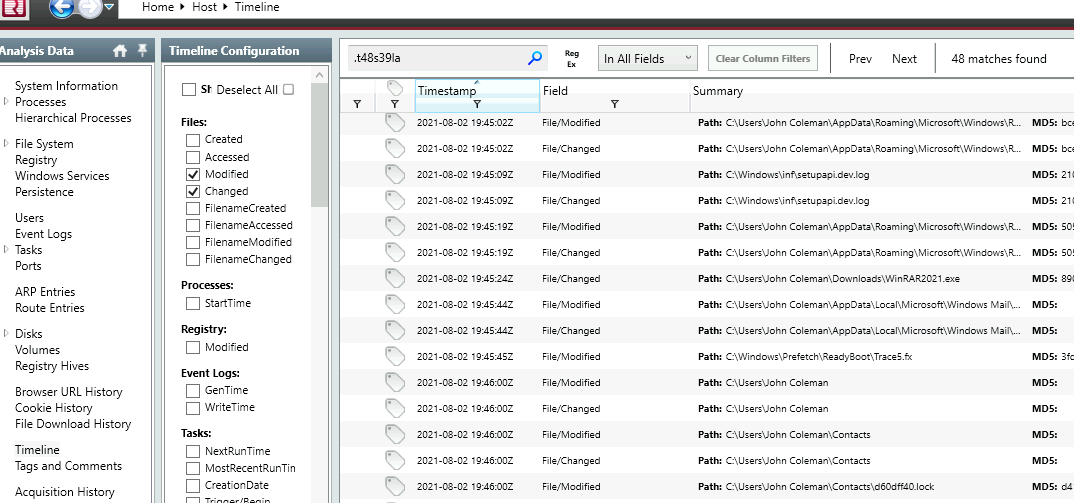
Head to ‘Timeline’ and see what files were renamed and changed.
Deselect the default filter and filter for ‘modified’ and ‘changed’ files.
In the search bar, search for files associated with the ‘.t48s39la’ extension.
Check top right edge.
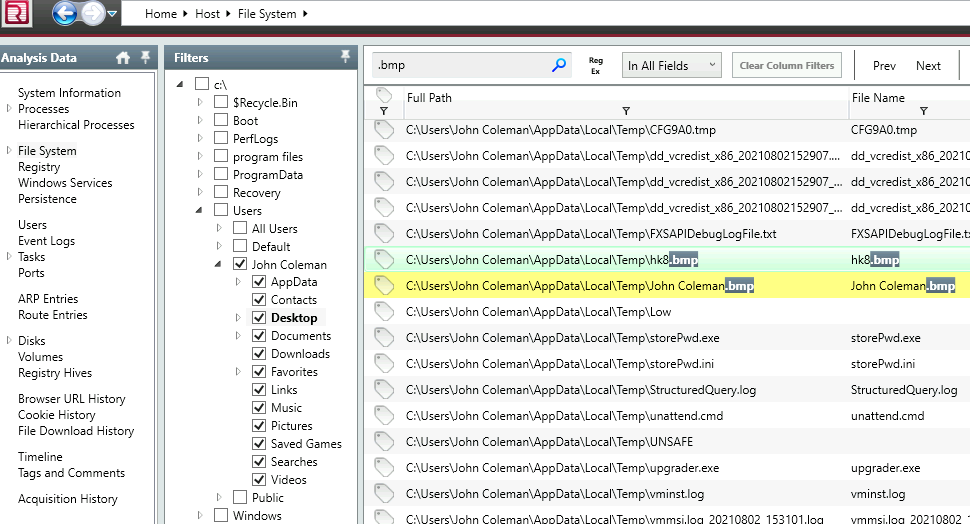
9. What is the full path to the wallpaper that got changed by an attacker, including the image name?
This one took a while.
Searching for a wallpaper files such as ‘.bmp’ file
Searches always come back with something.
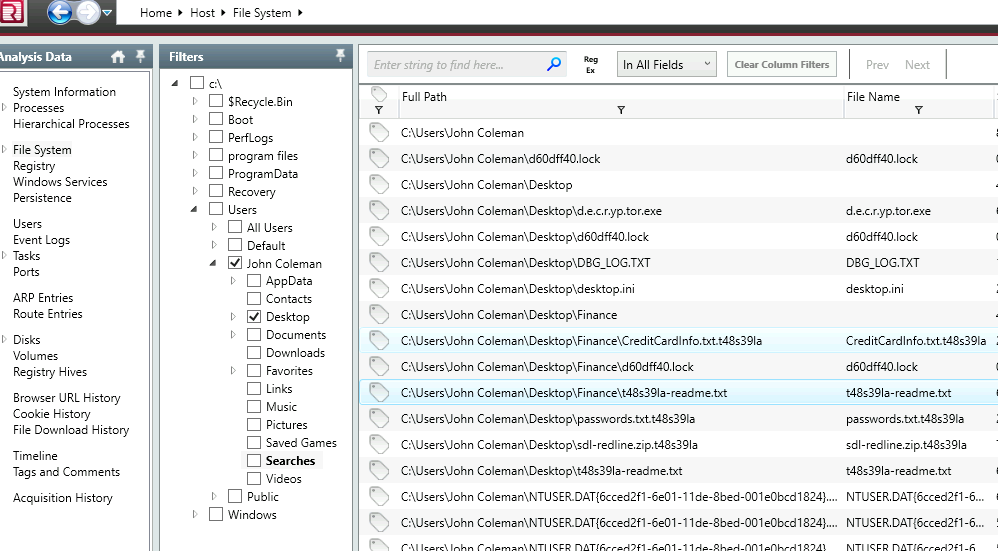
10. The attacker left a note for the user on the Desktop; provide the name of the note with the extension.
There’s a reason why they call themselves Readme files.
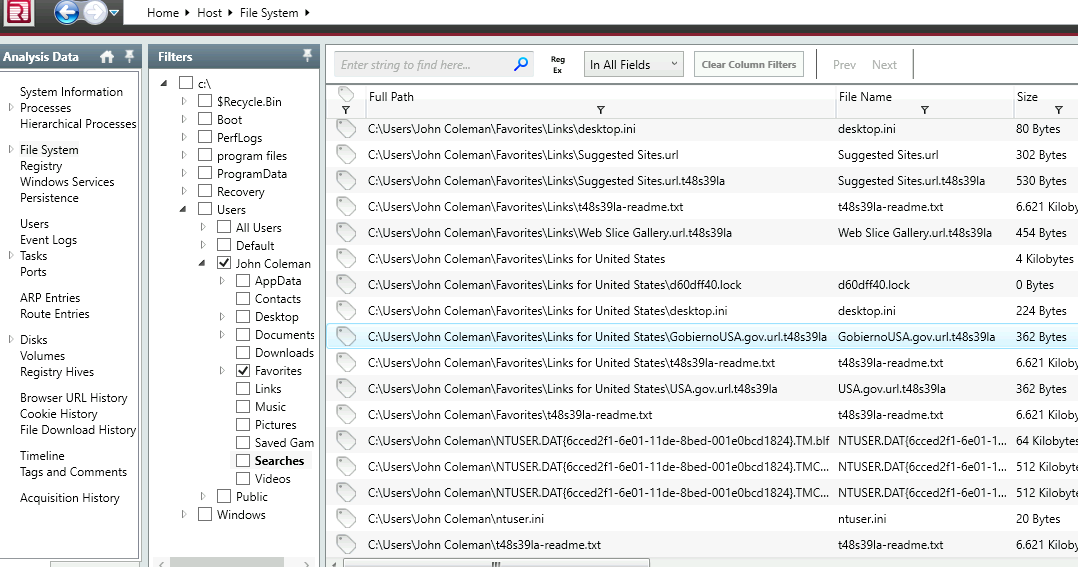
11. The attacker created a folder “Links for United States” under C:\Users\John Coleman\Favorites\ and left a file there. Provide the name of the file.
Let’s check that folder.
It must link to ‘USA’
12. There is a hidden file that was created on the user’s Desktop that has 0 bytes. Provide the name of the hidden file.
Applying our filter again to check the files in ‘Desktop’ we see some file of size 0 bytes.
I knew you would find it too.
13. The user downloaded a decryptor hoping to decrypt all the files, but he failed. Provide the MD5 hash of the decryptor file.
I saw some ‘decryp…’ file somewhere. Checked ‘Downloads’ folder but didn’t see it ,then ‘Desktop’
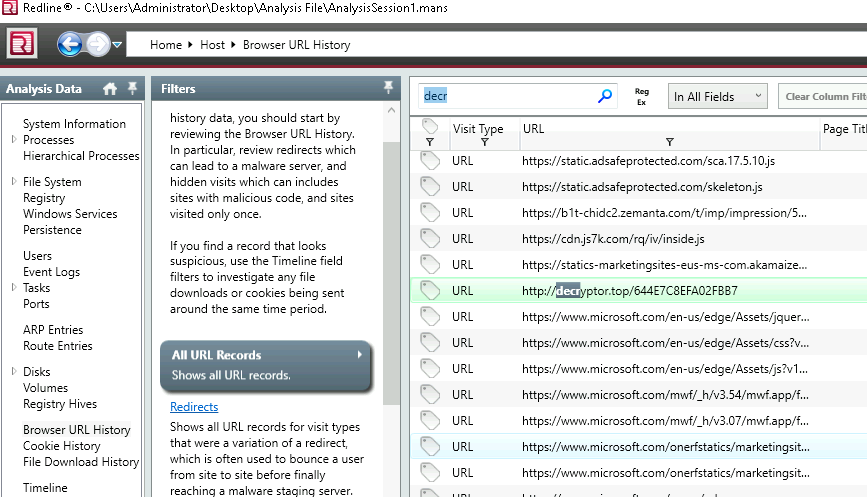
14. In the ransomware note, the attacker provided a URL that is accessible through the normal browser in order to decrypt one of the encrypted files for free. The user attempted to visit it. Provide the full URL path.
Headed to ‘Browser URL History’ and looked for ‘decry…’
Searches always work.
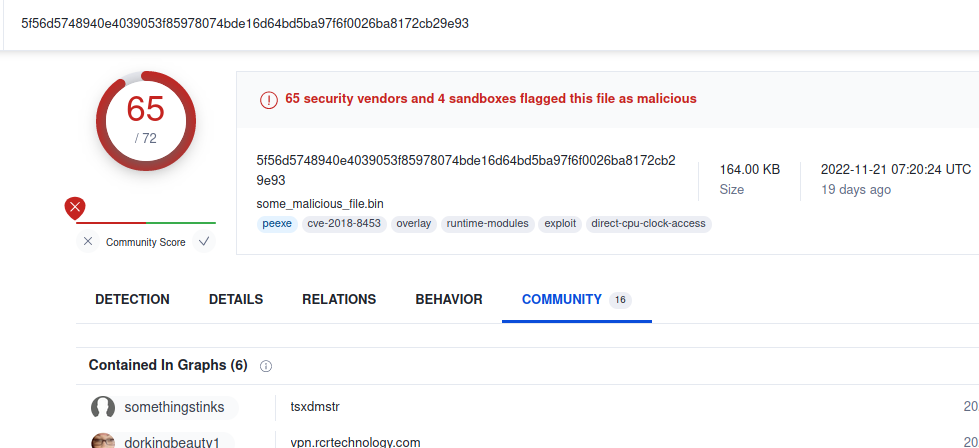
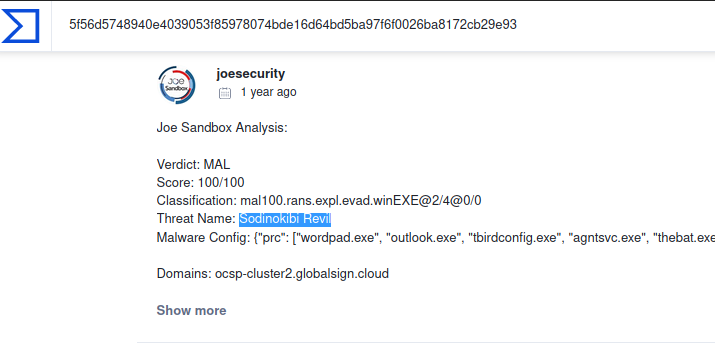
15. What are some three names associated with the malware which infected this host? (enter the names in alphabetical order)
This was quit easy.
Searched through VirusTotal for our MD5 hash of the binary And Checked through the community comments to find two common names.
Found the other name on mitre attack website.
Order will save you.
Well, There are many ways of killing a rat!
Happy Hacking.