A short write up for some ctf challenges held at KCA University during the intervarsity bootcamp by SheHacksKE, fr334aks, Safaricom, AfricaHackOn, Ekraal Innovation Hub, Trend Micro, Microsoft.
OSINT
Challenge: Hunter1
Given a SHA256 hash of a malicious office document, What’s the name of the ransomware behind the Malicious Office Document?
This was pretty easy.
Solution
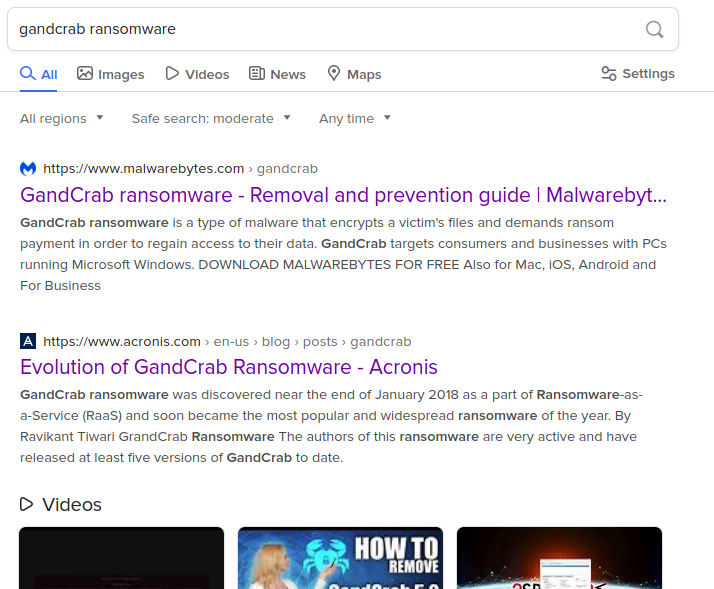
Searching the SHA256 hash on Google brings up a link highlighting “Gandcrab ransomware” and that’s it, you have hunted down the name of the ransomware.
flag{gandcrab}
Challenge: Last Hunt
This hunt was about the payment methods used by gandcrab. Other than BTC the Ransomware group also uses?
Solution
I did some googling on “gandcrab ransomware” and went through a few articles.
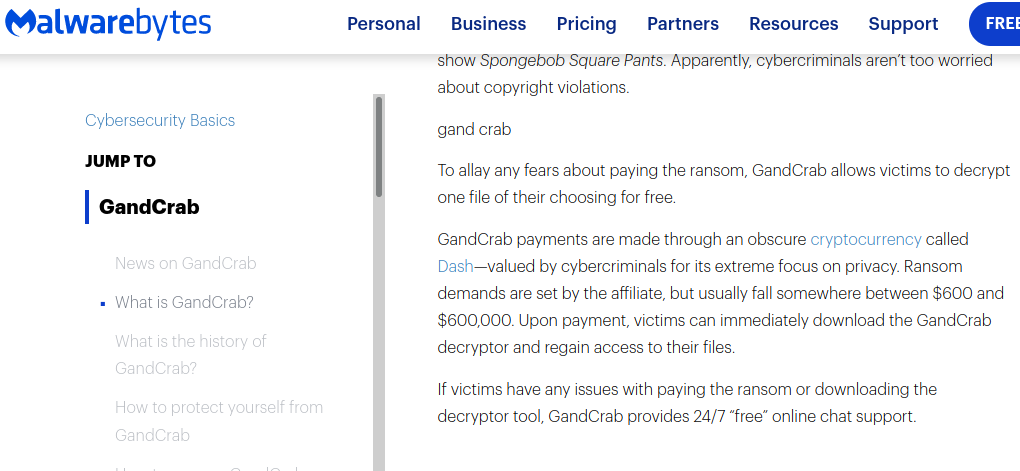
A story featured on malwarebytes (here) stated the payment method.
flag{dash}
Forensics
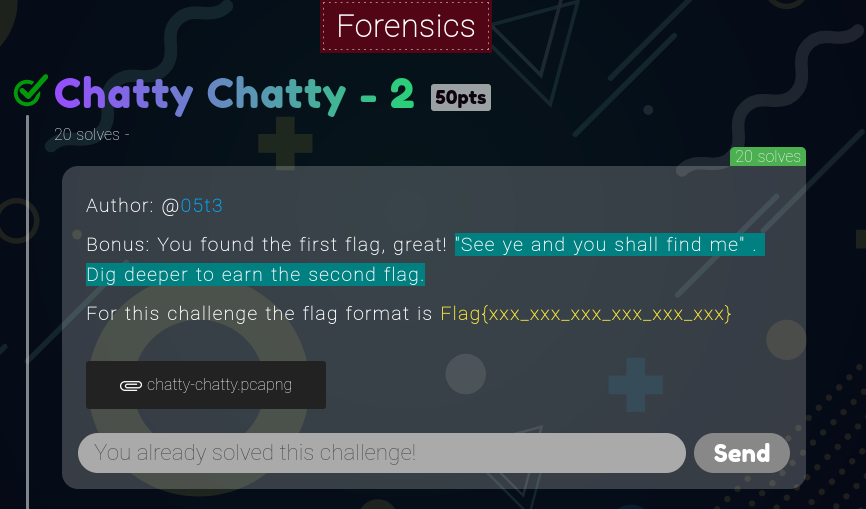
Challenge: Chatty Chatty — 2
“See ye and you shall find me”. Dig deeper to earn the second flag.
I didn’t get the first flag but here, I could “see and find”
I just saw and found.
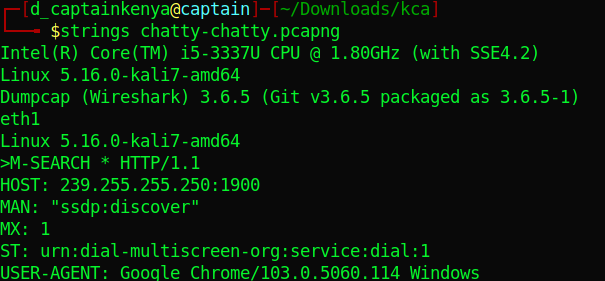
Download the given file.
Well, turns out there are many ways of killing a rat(including burning the whole house)
Solution
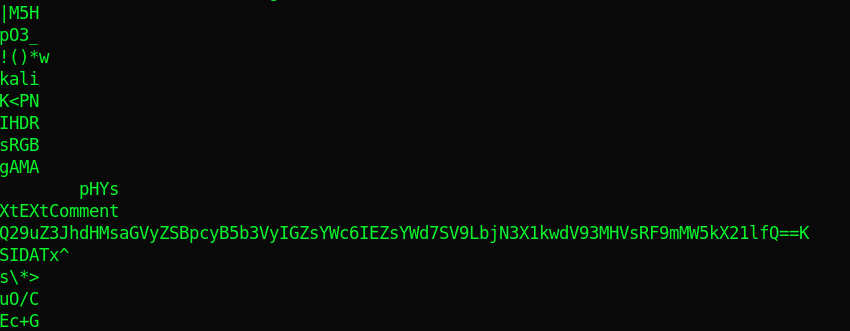
I ran strings on the file and found a base64 string.
I decoded the base64 string to get the flag.
Flag{I_Kn3w_Y0u_w0ulD_f1nd_me}
Similarly: Uploading the file at cyberchef also revealed the base64 without any recipe.
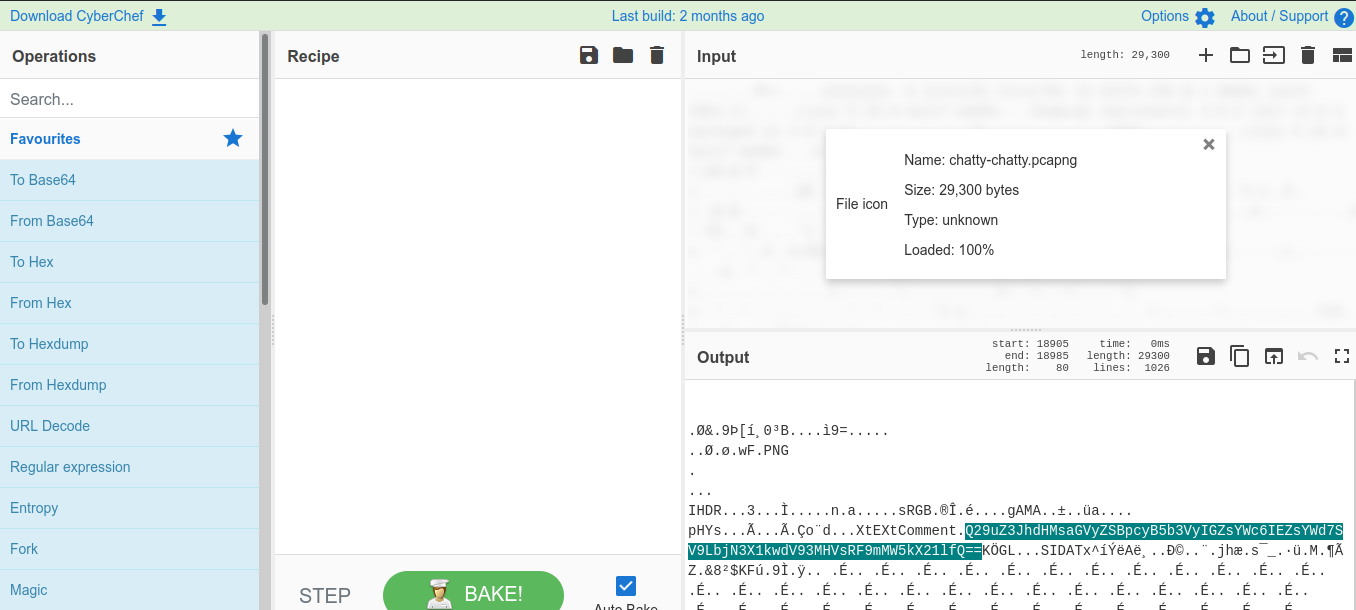 Go ahead and decode the string.
Go ahead and decode the string.
Similarly: The exiftool should reveal the base64 string as explained by oste here.
Turns out; There are many ways of killing a rat!
Happy Hacking.